Enhancing information security

Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2020 3rd Quarter (Jul. - Sep.)]
Release Date:Nov 25, 2020
IT Security Center
1. 2020 3rd Quarter: Vulnerability Countermeasure Information Database JVN iPedia Registration Status
The vulnerability countermeasure information database JVN iPedia (https://jvndb.jvn.jp/en/) is endeavoring to become a comprehensive vulnerability database where vulnerability information is aggregated for easy access for IT users. JVN iPedia collects and/or translates the vulnerability information published by 1) domestic software developers, 2) JVN (*1), a vulnerability information portal run by JPCERT/CC and IPA, and 3) NVD (*2), a vulnerability database run by NIST (*3). JVN iPedia has been making vulnerability information available to the public since April 25, 2007.
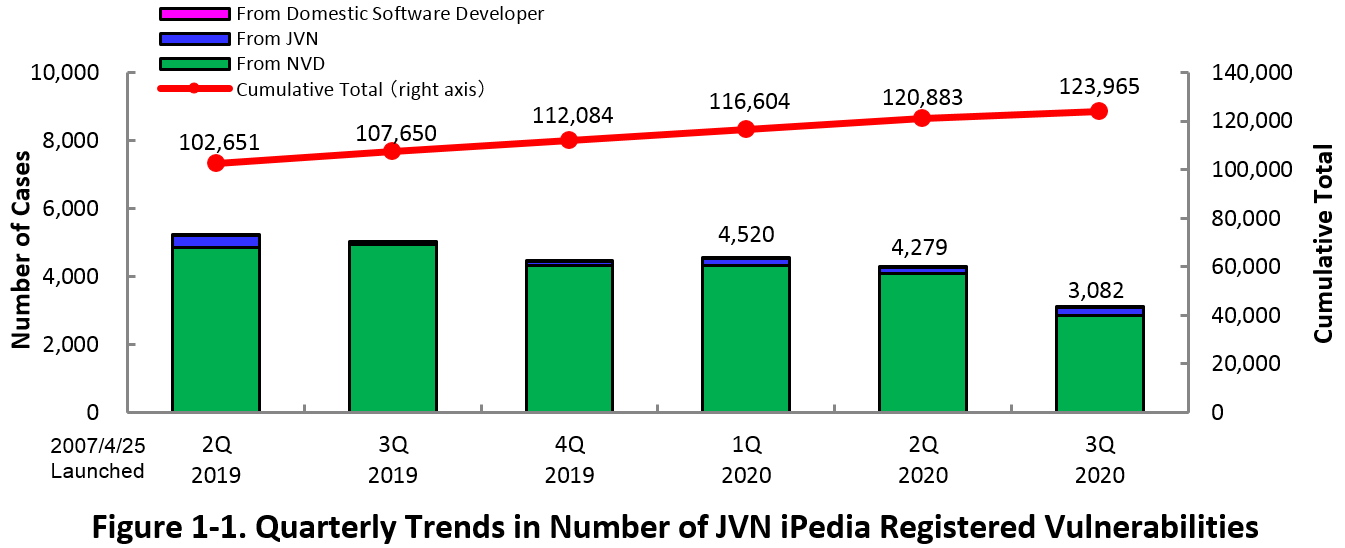
1-1. Vulnerabilities Registered in 2020/3Q
~ JVN iPedia now stores 123,965 vulnerabilities ~
The summary of the vulnerability information registered to the Japanese version of JVN iPedia during the 3rd quarter of 2020 (July 1 to September 30, 2020) is shown in the table below. As of the end of September 2020, the total number of vulnerabilities stored in JVN iPedia is 123,965 (Table 1-1, Figure 1-1).
As for the JVN iPedia English version, the total number of vulnerabilities stored is 2,188 as shown in the lower half of the Table 1-1.
Table 1-1. Vulnerabilities Registered to JVN iPedia during 3rd Quarter of 2020
|
|
Information Source
|
Registered Cases
|
Cumulative Cases
|
|---|---|---|---|
|
Japanese Version
|
Domestic Product Developers
|
4 cases
|
243 cases
|
|
JVN
|
232 cases
|
9,524 cases
|
|
|
NVD
|
2,846 cases
|
114,198 cases
|
|
|
Total
|
3,082 cases
|
123,965 cases
|
|
|
English Version
|
Domestic Product Developers
|
4 cases
|
241 cases
|
|
JVN
|
25 cases
|
1,947 cases
|
|
|
Total
|
29 cases
|
2,188 cases
|
2. Details on JVN iPedia Registered Data
2-1. Types of Vulnerabilities Reported
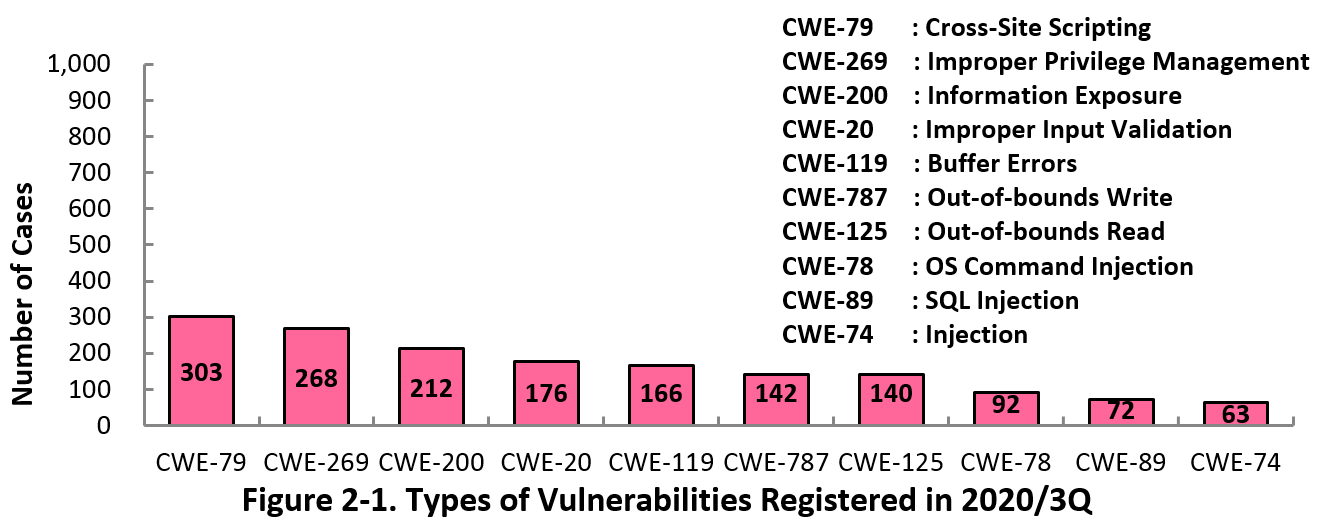
Figure 2-1 shows the number of vulnerabilities newly added to JVN iPedia during the 3rd quarter of 2020, sorted by the CWE vulnerability types.
The type of the vulnerabilities reported most in the 3rd quarter is CWE-79 (Cross-Site Scripting) with 303 cases, followed by CWE-269 (Improper Privilege Management) with 268, CWE-200 (Information Exposure) with 212, CWE-20 (Improper Input Validation) with 176, CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer) with 166.
CWE-79 (Cross-Site Scripting), the most reported vulnerability type in this quarter, could allow attackers to display false webpages and/or steal information.
Software developers need to make sure to mitigate vulnerability from the planning and design phase of software development. IPA provides tools and guidelines, such as "Vulnerability Countermeasure Guide for Software Developers"" (*4), "How to Secure Your Website" (*5), "Secure Programming Guide" (*6) and "AppGoat" (*7), a hands-on venerability learning tool, for website developers and operators to build secure websites.
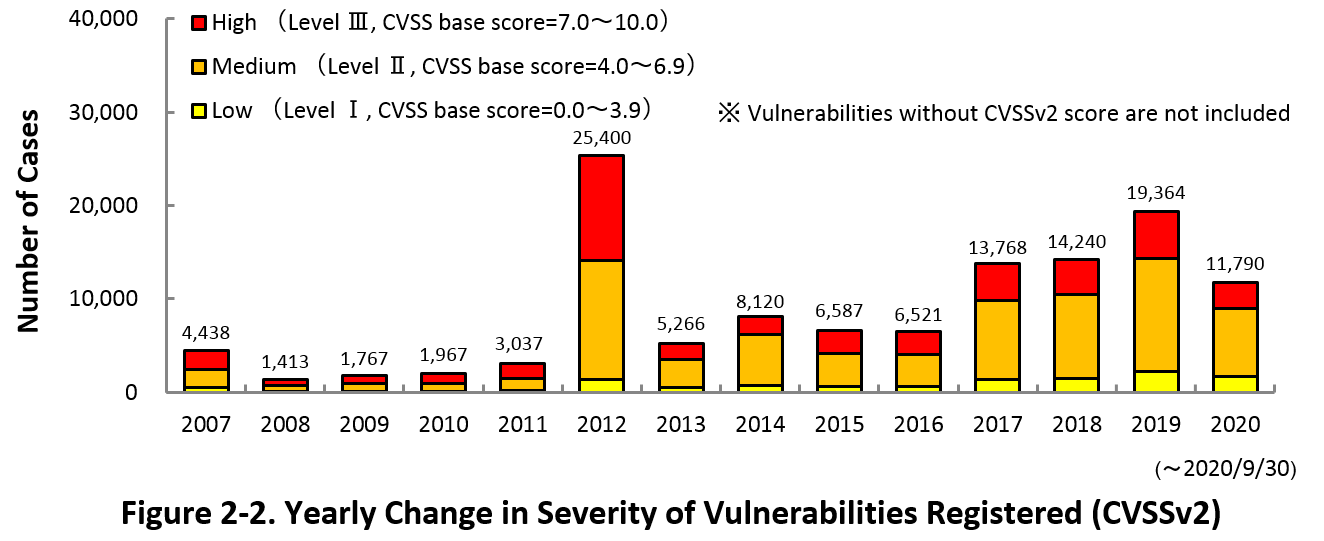
2-2. Severity of Vulnerabilities Reported
Figure 2-2 shows the yearly change in the CVSSv2 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2020, 24.0 percent are “Level III” (7.0 - 10.0), 61.7 percent are “Level ll” (4.0 – 6.9) and 14.3 percent are “Level I” (0.0 – 3.9). This means 85.7 percent of all vulnerabilities registered are Level II or higher, which are potentially critical enough to cause damage like information exposure or data falsification.
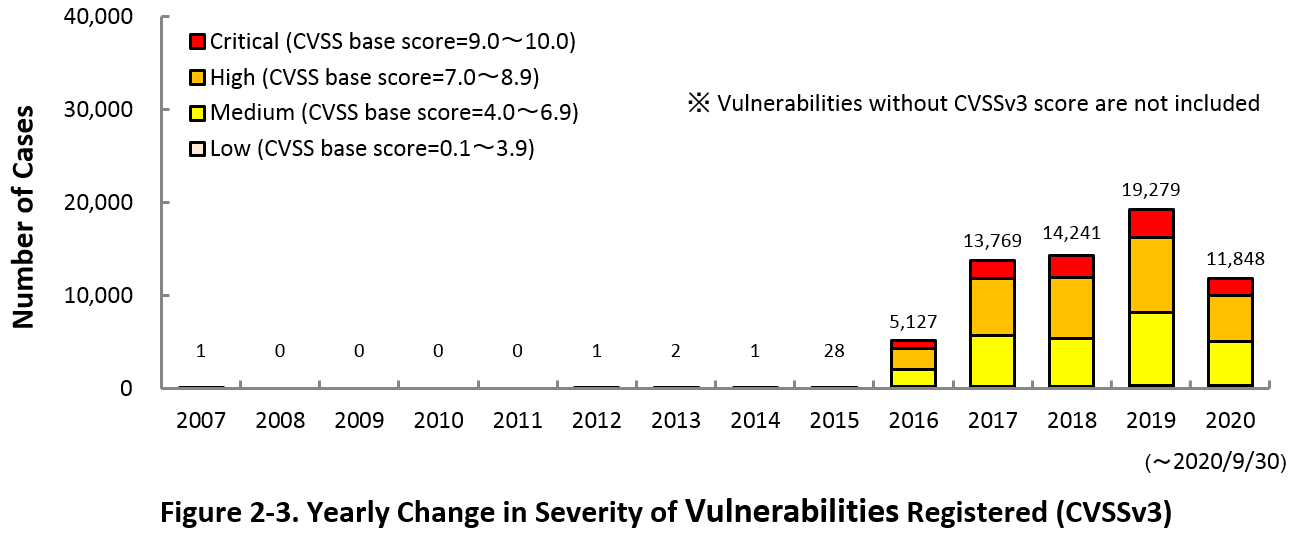
Figure 2-3 shows the yearly change in the CVSSv3 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2020, 15.5 percent are “Critical” (9.0 – 10.0), 42.1 percent are “High” (7.0 – 8.9), 40.4 percent are “Medium” (4.0 – 6.9) and 2.0 percent are “Low” (0.1 – 3.9).
To avoid threats posed by the known vulnerabilities, both product developers and IT users should pay close attention to vulnerability disclosure and update software they use to a fixed version or apply a security patch as soon as possible when they become available. IT users can check vulnerabilities newly published on JVN iPedia in RSS and XML format (*8) as well.
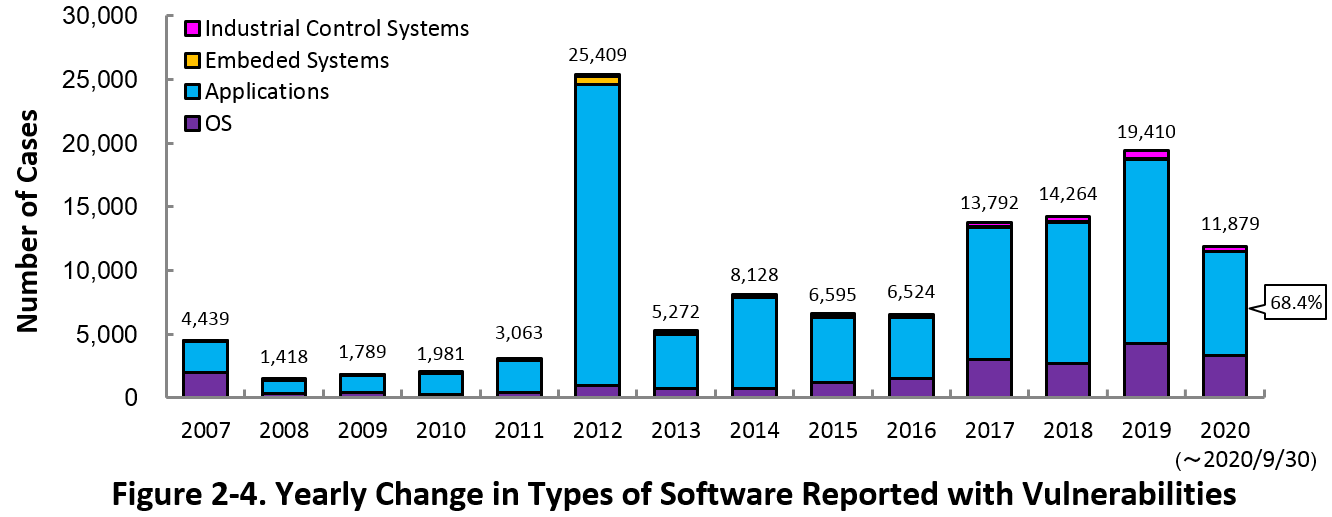
2-3. Types of Software Reported with Vulnerability
Figure 2-4 shows the yearly change in the type of software reported with vulnerability. Application vulnerabilities have been published most, accounting for 68.4 percent (8,126 out of 11,879) of the 2020 total.
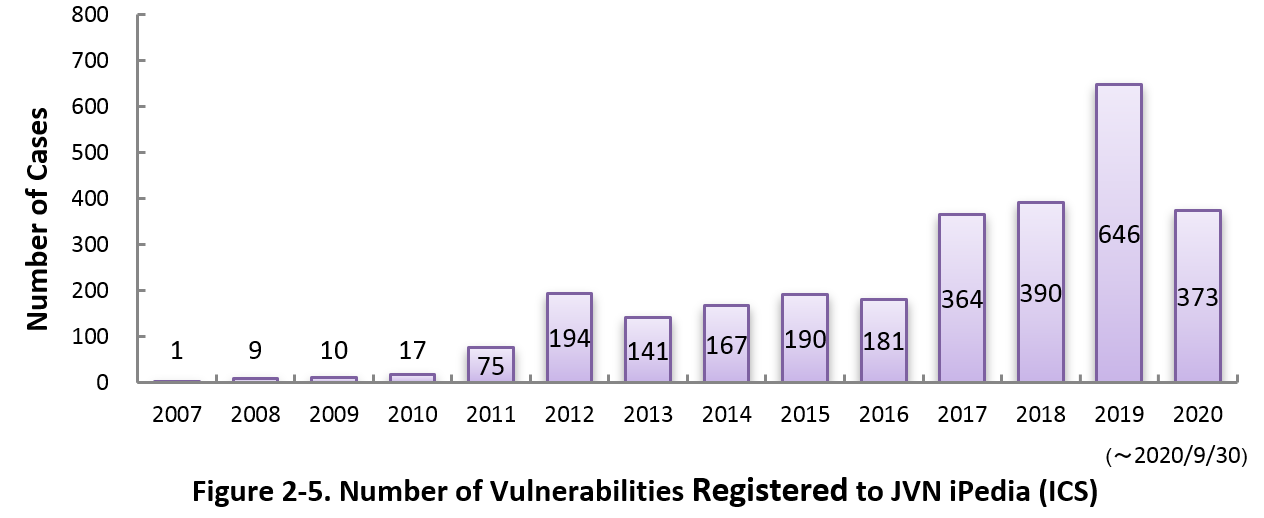
Figure 2-5 shows the yearly change in the number of JVN iPedia-stored vulnerabilities in industrial control systems (ICS) used in critical infrastructure sectors. As of September 2020, the total of 2,758 ICS vulnerabilities have been registered.
2-4. Products Reported with Vulnerability
Table 2-1 lists the top 20 software whose vulnerabilities were most registered to JVN iPedia during the 3rd quarter (July to September) of 2020.
In this quarter, the 1st rank continued to be Microsoft Windows 10 from the previous quarter. From 2nd to 20th, other Windows OS products are also ranked.
Besides those in the top 20 list, JVN iPedia stores and offers vulnerability information about a variety of software. IPA hopes software developers and users will make good use of JVN iPedia to efficiently check vulnerability information and take necessary action in a timely manner (*9).
Table 2-1. Top 20 Software Products Vulnerabilities Were Most Registered [Jul. – Sep. 2020]
|
Rank
|
Category
|
Product Name (Vendor)
|
Number of
Vulnerabilities Registered |
|---|---|---|---|
|
1
|
OS
|
Microsoft Windows 10 (Microsoft)
|
261
|
|
2
|
OS
|
Microsoft Windows Server (Microsoft)
|
243
|
|
3
|
OS
|
Microsoft Windows Server 2019 (Microsoft)
|
224
|
|
4
|
OS
|
Microsoft Windows Server 2016 (Microsoft)
|
187
|
|
5
|
OS
|
Android (Google)
|
140
|
|
6
|
OS
|
Microsoft Windows 8.1 (Microsoft)
|
129
|
|
6
|
OS
|
Microsoft Windows RT 8.1 (Microsoft)
|
129
|
|
8
|
OS
|
Microsoft Windows Server 2012 (Microsoft)
|
126
|
|
9
|
OS
|
Microsoft Windows 7 (Microsoft)
|
113
|
|
10
|
OS
|
Microsoft Windows Server 2008 (Microsoft)
|
108
|
|
11
|
PDF Viewer/Editor
|
Adobe Acrobat (Adobe Systems)
|
50
|
|
11
|
PDF Viewer/Editor
|
Adobe Acrobat DC (Adobe Systems)
|
50
|
|
11
|
PDF Viewer
|
Adobe Acrobat Reader DC (Adobe Systems)
|
50
|
|
14
|
Firmware
|
Qualcomm component (Qualcomm)
|
49
|
|
15
|
OS
|
iOS (Apple)
|
42
|
|
15
|
OS
|
iPadOS (Apple)
|
42
|
|
17
|
OS
|
Apple Mac OS X (Apple)
|
41
|
|
18
|
Server Management Software
|
CentOS Web Panel (CentOS Web Panel)
|
39
|
|
19
|
Web-based collaborative platform
|
Microsoft SharePoint Server (Microsoft)
|
35
|
|
20
|
Web-based collaborative platform
|
Microsoft SharePoint Enterprise Server (Microsoft)
|
34
|
3. Most Accessed Vulnerability Countermeasure Information
Table 3-1 lists the top 20 most accessed vulnerability countermeasure information in JVN iPedia during the 3rd quarter of 2020 (July to September).
In this quarter, the 1st rank is the vulnerability countermeasure information of phpMyAdmin, which was published in 2014. This was due to a large number of accesses that appeared to be mechanical from a certain organization.
Six of top 20 (8th, 12th, 13th, 15th, 18th, and 19th) are vulnerability countermeasure information related to Hitachi products. Since these products attract a lot of attention from users in Japan, the number of access to these pages tends to increase.
Rating Scale
Note 1) CVSSv2 Severity Rating Scale
- Level I (Low)
- CVSS Base Score = 0.0~3.9
- Level II (Medium)
- CVSS Base Score = 4.0~6.9
- Level III (High)
- CVSS Base Score = 7.0~10.0
Note 2) CVSSv3 Severity Rating Scale
- Low
- CVSS Base Score =0.1~3.9
- Medium
- CVSS Base Score =4.0~6.9
- High
- CVSS Base Score =7.0~8.9
- Critical
- CVSS Base Score =9.0~10.0
Table 3-1. Top 20 Most Accessed Vulnerability Countermeasure Information in JVN iPedia [Jul. – Sep. 2020]
No.1 phpMyAdmin vulnerable to cross-site scripting JVNDB-2014-003893
- CVSSv2 Severity Rating Scale
-
- Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Base Score
-
-
- Date Public
-
2014/8/25
- Access Count
-
7,058
No.2 Android App "Mercari" (Japan version) vulnerable to arbitrary method execution of the Java object JVNDB-2020-000043
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
5.1
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.0
- Date Public
-
2020/7/8
- Access Count
-
6,778
No.3 WordPress Plugin "Social Sharing Plugin" vulnerable to cross-site request forgery JVNDB-2020-000046
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2020/7/22
- Access Count
-
6,741
No.4 Multiple vulnerabilities in TCP/IP function on Mitsubishi Electric GOT2000 series JVNDB-2020-006469
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2020/7/9
- Access Count
-
6,651
No5. TOYOTA MOTOR's Global TechStream vulnerable to buffer overflow JVNDB-2020-000049
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.4
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.1
- Date Public
-
2020/7/29
- Access Count
-
6,613
No.6 SKYSEA Client View vulnerable to privilege escalation JVNDB-2020-000052
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
- High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2020/8/3
- Access Count
-
6,594
No.7 SHIRASAGI vulnerable to open redirect JVNDB-2020-000045
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.7
- Date Public
-
2020/7/9
- Access Count
-
6,476
No.8 Server Side Request Forgery Vulnerability in Hitachi Ops Center Analyzer viewpoint JVNDB-2020-006586
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/7/13
- Access Count
-
6,072
No.9 Multiple vulnerabilities in multiple PHP Factory products JVNDB-2020-000051
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.8
- Date Public
-
2020/7/31
- Access Count
-
5,910
No.10 FANUC i Series CNC vulnerable to denial-of-service (DoS) JVNDB-2020-000050
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2020/7/31
- Access Count
-
5,904
No.11 JavaFX WebEngine does not properly restrict Java method execution JVNDB-2020-000047
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
- High
- CVSSv3 Base Score
-
8.8
- Date Public
-
2020/7/28
- Access Count
-
5,833
No.12 Cross-site Scripting Vulnerability in Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center Analyzer JVNDB-2020-006617
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/7/14
- Access Count
-
5,741
No.13 DoS Vulnerability in Hitachi Device Manager JVNDB-2020-006031
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/6/29
- Access Count
-
5,637
No.14 Chrome Extension for e-Tax Reception System vulnerable to arbitrary command execution JVNDB-2020-000040
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.1
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.0
- Date Public
-
2020/6/24
- Access Count
-
5,359
No.15 DoS Vulnerability in HiRDB JVNDB-2020-007128
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/8/3
- Access Count
-
5,239
No.16 Multiple vulnerabilities in Cybozu Garoon JVNDB-2020-000042
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
5.5
- CVSSv3 Severity Rating Scale
-
- High
- CVSSv3 Base Score
-
8.5
- Date Public
-
2020/6/29
- Access Count
-
5,235
No.17 Mitsubishi Electric MELSEC iQ-R, iQ-F, Q, L, and FX series vulnerable to cleartext transmission of sensitive information JVNDB-2020-005854
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
10.0
- Date Public
-
2020/6/24
- Access Count
-
5,126
No.18 Multiple Vulnerabilities in Hitachi Command Suite, Hitachi Automation Director, Hitachi Configuration Manager, Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center JVNDB-2020-007127
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/8/3
- Access Count
-
5,105
No.19 Vulnerability in Cosminexus HTTP Server JVNDB-2020-005743
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/6/22
- Access Count
-
5,063
No.20 NITORI App fails to restrict access permissions JVNDB-2020-000057
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2020/8/26
- Access Count
-
5,019
Table 3-2 lists the top 5 most accessed vulnerability information among those reported by domestic product developers.
Table 3-2. Top 5 Most Accessed Vulnerabilities Reported by Domestic Product Developers [Jul. - Sep. 2020]
No.1 Server Side Request Forgery Vulnerability in Hitachi Ops Center Analyzer viewpoint JVNDB-2020-006586
- CVSSv2 Base Score
-
- -
- CVSSv3 Base Score
-
- -
- Date Public
-
2020/7/13
- Access Count
-
6,072
No.2 Cross-site Scripting Vulnerability in Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center Analyzer JVNDB-2020-006617
- CVSSv2 Base Score
-
- -
- CVSSv3 Base Score
-
-
- Date Public
-
2020/7/14
- Access Count
-
5,741
No.3 DoS Vulnerability in Hitachi Device Manager JVNDB-2020-006031
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/6/29
- Access Count
-
5,637
No.4 DoS Vulnerability in HiRDB JVNDB-2020-007128
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/8/3
- Access Count
-
5,239
No.5 Multiple Vulnerabilities in Hitachi Command Suite, Hitachi Automation Director, Hitachi Configuration Manager, Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center JVNDB-2020-007127
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2020/8/3
- Access Count
-
5,105
Footnotes
-
(*1)
-
(*2)
-
(*3)
-
(*4)
-
(*5)
-
(*6)
-
(*7)
-
(*8)
-
(*9)
Past Quarterly Reports
Contact information
IT Security Center, Information-technology Promotion Agency, Japan (ISEC/IPA)