Enhancing information security

Vulnerabilities:CCE (Common Platform Enumeration) Overview
Last Updated:Sep 24, 2010
IT Security Center
Information-technology Promotion Agency, Japa
The Identification of Security-Related Configuration Issues Using a Common Identifier Scheme
>> JAPANESE
CCE (Common Configuration Enumeration)(*1)is a specification in which unique, common identification numbers are allotted to security-related configuration issues to clarify the issues.
CCE is a component of SCAP (Security Content Automation Protocol)(*2), which is a set of technical specifications promoted by the U.S. government to support standardization and automation of information security implementation. CCE has been developed through the leadership of MITRE(*3)with the support of the U.S. government, and the first draft, which addressed 533 security-related configuration issues for Windows2000, Windows XP and Windows Server 2003, was released in August 2007. Its coverage expanded to 914 issues in the version 4.0 released in July 2007. After the version 5, released in December 2007, the security-related configuration issues have been organized by application platforms.
CCE provides a list of security-related configuration issues that need to be considered to ensure the baseline security for a computer system, and one can use it to check whether a computer system痴 security settings are appropriately configured. Adoption of CCE will enable venders, security experts, system administrators and users to identify and discuss security-related configuration issues on various IT platforms through a common language.
This overview is based on CCE Creation Process (http://cce.mitre.org/lists/creation_process.html) released on July 28, 2008, and CCE List (CCE Version 5.2 compliant) (http://cce.mitre.org/lists/cce_list.html) released on April 28, 2010. For more information on CCE, please refer to both of these documents.
1.CCE Identifier Number (CCE-ID)
CCE assigns unique, common identification numbers (CCE ID) to security-related configuration issues to clarify the issues. A CCE ID consists of the format of 鼎CE-identifier-check digit�. An identifier is allotted randomly and a check digit is generated according to the Luhn Check Digit Algorithm to detect errors.
Security-related configuration issues are defined by CCE Working Group with the cooperation of OS vendors based on the existing security guidelines and monitoring tools, for example, Microsoft Windows Server 2008 Security Guide, Microsoft Office 2007 Security Guide, security configuration benchmarks by CIS (Center for Internet Security)(*4), security checklists by NIST (National Institute of Standards and Technology)(*5), security guidelines by NSA (National Security Agency)(*6)and security implementation guidelines by DISA (Defense Information Systems Agency)(*7).
Examples of security-related configuration issues are those related to auditing and account management policy, such as user privilege and password settings, and those related to network services, including starting server programs and authorization settings. For example, Windows XP has various password settings, such as its minimum length, maximum age, and history control (the number of unique, new passwords that have to be associated with a user account before the user can reuse an old password). The table below shows a recommended value for the Windows XP password settings suggested by FDCC (Federal Desktop Core Configuration), DISA and Microsoft痴 security guides.
|
CCE-ID
|
Security-Related
Configuration Issue
|
FDCC(*a)
|
DISA(*b)
|
Microsoft(*c)
|
|
CCE-2981-9
|
Minimum Password Length
|
12 or more characters |
14 or more characters |
8 or more characters |
|
CCE-2920-7
|
Maximum Password Age
|
60 or less days
|
60 or less days
|
90 or less days
|
|
CCE-2994-2
|
Enforce Password History (the number of unique, new passwords before an old password can be reused) |
24 or more
|
24 or more
|
24 or more
|
|
CCE-2439-8
|
Minimum Password Age
|
1 or more days
|
1 or more days
|
1 or more days
|
|
CCE-2986-8
|
Account Lockout Threshold (the maximum number of failed attempts that can occur before the account is locked out) |
5 or less times
|
3 or less times
|
50 or less times
|
|
CCE-2466-1
|
Reset Account Lockout Counter After |
15 or more minutes |
60 or more minutes |
15 or more minutes |
|
CCE-2928-0
|
Account Lockout Duration (how long the user account should be locked out) |
15 or more minutes |
Permanent
|
15 or more minutes |
|
CCE-2980-1
|
Screen Lock (Screen Saver Timeout) |
15 or less minutes |
15 or less minutes |
-
|
|
CCE-4500-5
|
Password-Protected Screen Saver |
Required
|
Required
|
-
|
Table 1. CCE ID and Recommended Value
for Windows XP Password Settings
-
(*a)Recommended values defined in FDCC Version 1.2 Windows XP, released on April 8, 2009.
-
(*b)Recommended values defined in Windows XP STIG, Version 6, Release 1.17, published by DISA on April 23, 2010.
-
(*c)Recommended values defined in XPG-EC-Domain 1.01.0 (Enterprise Client environment) for Microsoft Security Compliance Manager for Windows XP SP3.
Password settings in other operating systems can be different in number. Table 2 shows a recommended value for the password settings for Red Hat Enterprise Linux 5 suggested by the NSA and CIS security guidelines.
|
CCE-ID
|
Security-Related Configuration Issue
|
NSA(*d)
|
CIS(*e)
|
|
CCE-4154-1
|
Minimum Password Length
|
8 or more characters |
8 or more characters |
|
CCE-4092-3
|
Maximum Password Age
|
60 or less days
|
90 or less days
|
|
CCE-4180-6
|
Minimum Password Age
|
7 or more days
|
7 or more days
|
|
CCE-3410-8
|
Account Lockout Threshold (the maximum number of failed attempts that can occurbefore the account is locked out) |
5 or less times
|
3 or less times
|
|
CCE-3315-9
|
Screen Lock (Screen Saver Timeout)
|
15 or less minutes
|
-
|
Table 2. CCE ID and Recommended Value
for Red Hat Enterprise Linux 5 Password Settings
-
(*d)Recommended values defined in Guide to the Secure Configuration of Red Hat Enterprise Linux 5 (Revision 3), released by NSA on October 21, 2009.
-
(*e)Recommended values defined in Security Configuration Benchmark For Red Hat Enterprise Linux 5 (Version 1.1.2), released by CIS in June 2009.
2.CCE List
Assignment of CCE IDs has begun in 2006, and as of April 2010 (Ver. 5.20100428), the security-related configuration issues for the following application platforms have been allotted with CCE IDs.
- Microsoft Office 2007
- Internet Explorer 7
- Windows 7/Windows Vista/Windows XP/Windows 2000/Windows Server 2008/Windows Server 2003
- Red Hat Enterprise Linux 5/Red Hat Enterprise Linux 4
- Sun Solaris 10/Sun Solaris 9/Sun Solaris 8
- AIX 5.3
- HP-UX 11.23
MITRE provides a list of CCE IDs for each application platform in the Excel format at the CCE website (http://cce.mitre.org) (Figure1 and Figure 2).
-
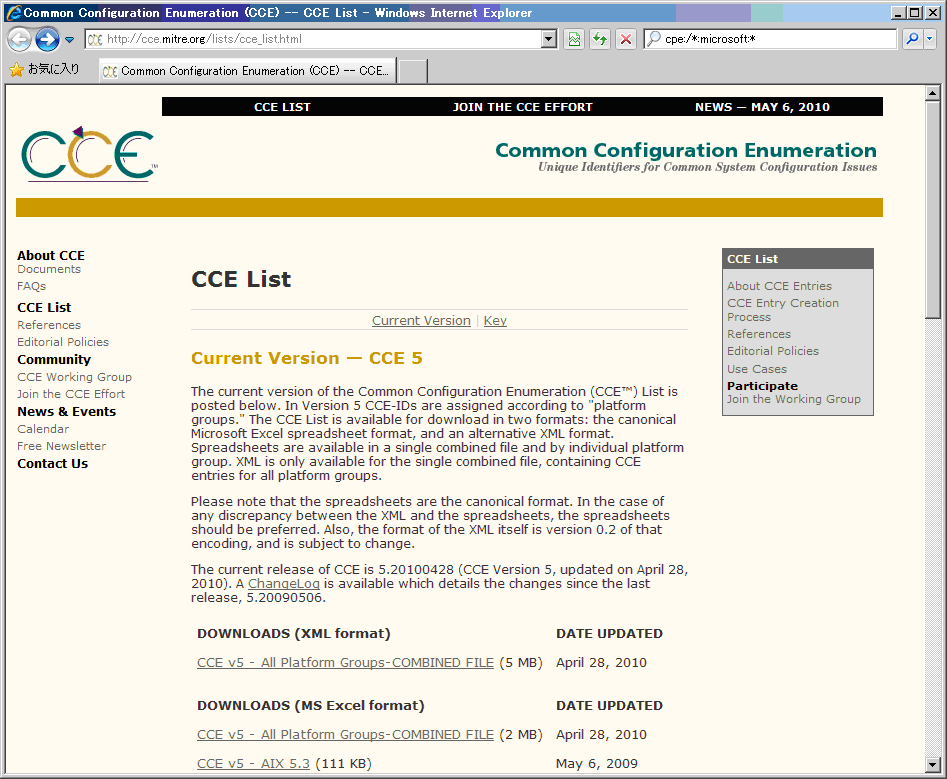
Figure1.CCE ID lists for application platforms listed at the CCE website -
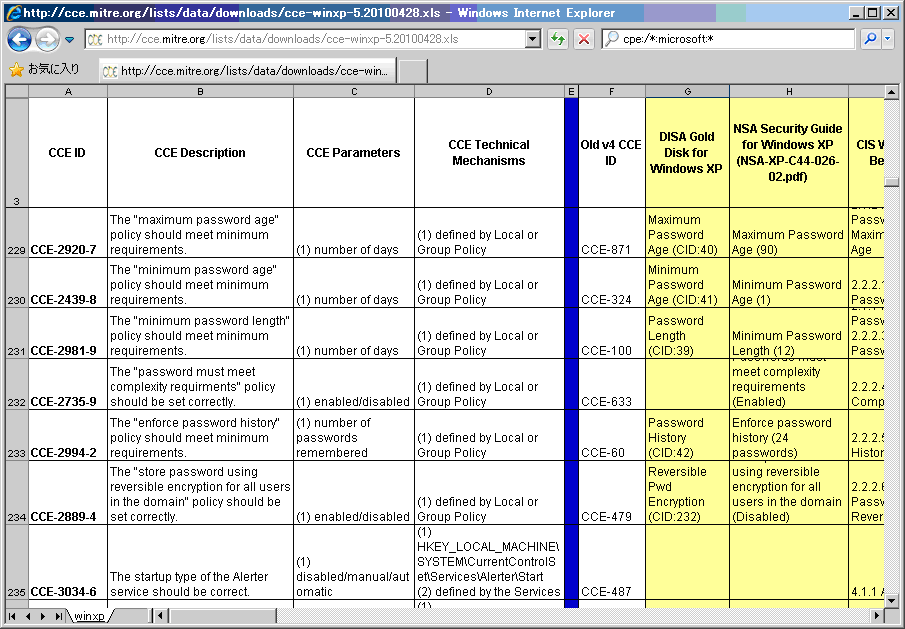
Figure2.CCE List for Windows XP
(1)CCE ID
A unique identifier number assigned to a security-related configuration issue.
(2)CCE Description
Explains what security-related configuration issue it is addressing.
(3)CCE Parameters
Defines the expected type of a value to be set. In case of CCE-2920-7 (Maximum Password Age), it tells that the value should be specified as the number of days.
(4)CCE Technical Mechanisms
Explains where or how to check the configuration setting technically. In case of CCE-2920-7 (Maximum Password Age), it tells that it can be checked by looking up the Local/Group Policy settings.
(5)References
Gives a list of references on the issue. For Windows XP, DISA Gold Disk for Windows XP, NSA Windows XP Security Guide, CIS Windows XP Professional Benchmark, NIST 800-68: Guidance for Securing Microsoft Windows XP Systems for IT Professional, FDCC Windows XP, and FDCC Windows XP Firewall are referenced. For Red Hat Enterprise Linux 5, Guide to the Secure Configuration of Red Hat Enterprise Linux 5 is referenced.
3.Security-Related Configuration Guideline
Major guidelines referenced in CCE are developed and maintained as checklist or benchmarks by the organizations listed below.
3.1 NIST
- Security Configuration Guides
- http://www.nsa.gov/ia/guidance/security_configuration_guides/index.shtml
NSA Security Configuration Guides are the security checklists developed and maintained by NSA. Platforms covered include databases (Oracle, Microsoft SQL Server), OS (Mac OX, Linux, Windows, Solaris), Web servers (Microsoft IIS), routers, IPv6 security, VoIP and wireless security.
3.2 DISA
- Security Checklists
- http://iase.disa.mil/stigs/checklist/index.html
DISA Security Checklists are the security checklists developed and maintained by DISA. Platforms covered include databases (Oracle, Microsoft SQL Server), OS (Windows, UNIX), Web servers (Apache, Tomcat, Microsoft IIS, WebLogic), anti-virus software, biometrics, Bluetooth, wireless security, DNS and Storage Area Network security.
3.3 NSA
- Security Configuration Guides
- http://www.nsa.gov/ia/guidance/security_configuration_guides/index.shtml
NSA Security Configuration Guides are the security checklists developed and maintained by NSA. Platforms covered include databases (Oracle, Microsoft SQL Server), OS (Mac OX, Linux, Windows, Solaris), Web servers (Microsoft IIS), routers, IPv6 security, VoIP and wireless security.
3.4 CIS
- CIS Benchmarks
- http://cisecurity.org/en-us/?route=downloads.benchmarks
CIS Benchmarks are the security checklists developed and maintained by CIS. Platforms covered include databases (Oracle, Microsoft SQL Server, MySQL), OS (Mac OX, FreeBSD, HP-UX, IBM AIX, Red Hat, Windows), Web servers (Apache, Microsoft IIS), virtualization software (VMware, Xen) and wireless security.
3.5 Microsoft
- Windows Vista Security Guide
- http://technet.microsoft.com/en-us/library/bb629420.aspx
- Windows XP Security Guide
- http://technet.microsoft.com/ja-jp/library/dd362935.aspx (Japanese)
- Microsoft Security Compliance Manager
- http://technet.microsoft.com/en-us/library/cc677002.aspx
Those listed above are security guides developed and maintained by Microsoft. Besides Windows Vista and Windows XP, security guides for other platforms, such as Microsoft Office 2007, are available. Microsoft Security Compliance Manager, a security management tool associated with those guides, is also available to manage and monitor baseline security in Windows.
Footnote
-
(*1)CCE:Common Configuration Enumeration. A unique, common identification number (CCE ID) to clarify and identify security-related configuration issues.
-
(*2)SCAP: Security Content Automation Protocol. A set of technical specifications supported by the U.S. government to promote standardization and automation of information security implementation.
-
(*3)MITRE Corporation: A not-for-profit organization that provides information technology support and research and development to the U.S. government.
-
(*4)CIS:Center for Internet Security:A nonprofit organization that support IT security risk mitigation in business and e-commerce.
-
(*5)National Institute of Standards and Technology. A federal agency that develops and promotes measurement, standards and technology.
-
(*6)National Security Agency. A U.S. intelligence agency under Department of Defense.
-
(*7)Defense Information Systems Agency. A U.S. agency that provides information technology and communications support to Department of Defense including military services.
Contact information
IT Security Center,
Information-technology Promotion Agency, Japan (ISEC/IPA)
-
E-mail