Enhancing information security

Information Security Early Warning Partnership
About Information Security Early Warning Partnership
In July 2004, the notice from the Ministry of Economy, Trade and Industry on “Standards for Handling Software Vulnerability Information and Others” was issued to ensure appropriate handling of vulnerability-related information when a vulnerability is reported, in order to reduce the damages that could be caused by unauthorized computer access or viruses. Based on these standards, the “Information Security Early Warning Partnership Guideline” (hereinafter, “the Guideline“) defining the recommended actions for relevant parties was established to achieve an appropriate flow of vulnerability-related information*1. Specifically, the Information-Technology, Promotion Agency (IPA) serves as the vulnerability reporting organization, while the Japan Computer Emergency Response Team Coordination Center (JPCERT/CC) serves as the coordinating organization. These organizations make efforts to handle vulnerability-related information properly with all relevant parties, including discoverers, software developers and website operators. This process is in alignment with ISO/IEC 29147:2014 “Vulnerability disclosure”.
- Notice from the Ministry of Economy, Trade and Industry
- Information Security Early Warning Partnership Guideline
- Information Security Early Warning Partnership Guideline Overview
*1) Vulnerability-related information: Information on vulnerabilities (technical details and characteristics), verification methods or methods of attack.
Scope of Information Security Early Warning Partnership
The guideline covers vulnerabilities that may affect a large number of people; specifically, in software products widely used in Japan and web applications that run on websites presumed to be accessed primarily from Japan (for example, websites written in Japanese, URLs that use the “jp” domain and so on). This document has been prepared to provide the relevant parties an overview of the guideline, describing how vulnerability-related information should be handled. The table below shows the advantages of being a part of the Information Security Early Warning Partnership. These efforts can reduce the likelihood that software users and website operators will become victims of attacks due to vulnerabilities.
| Relevant Parties |
Advantages of Information Security Early Warning Partnership |
|---|---|
| Discoverers |
|
| Software Developers |
|
| Website Operators |
|
-
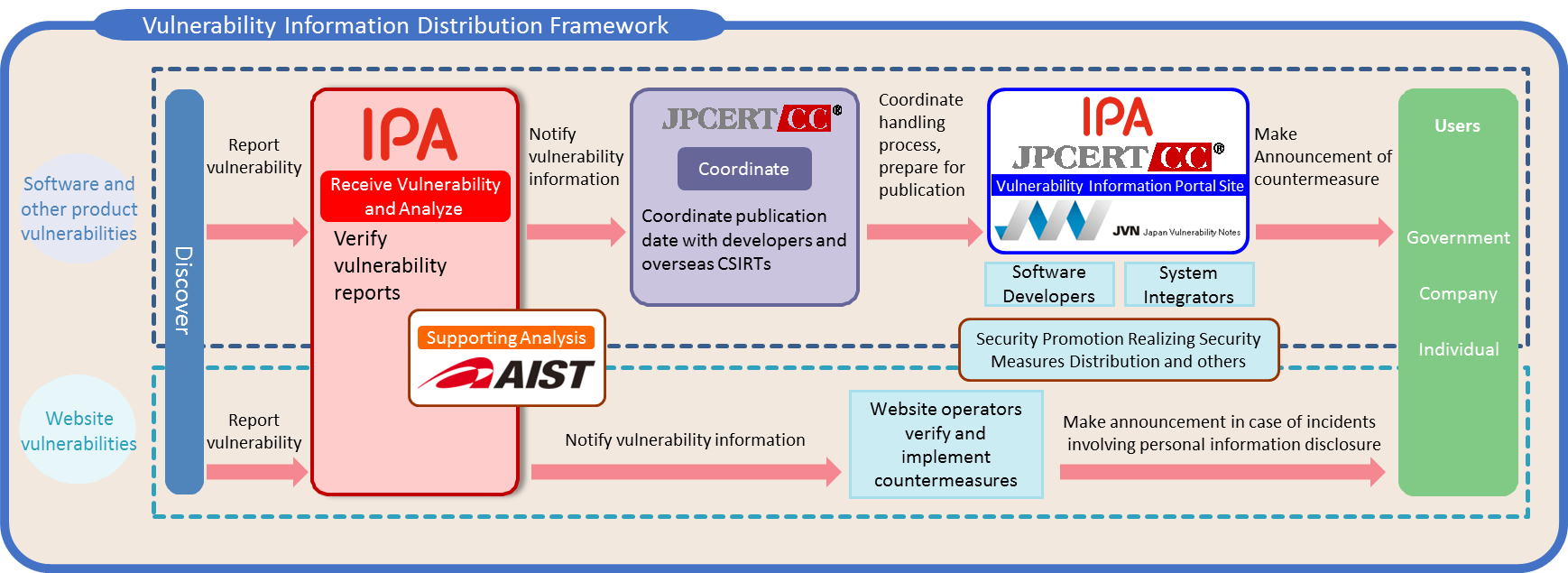
* JPCERT/CC: Japan Computer Emergency Response Team Coordination Center AIST: National Institute of Advanced Industrial Science and Technology
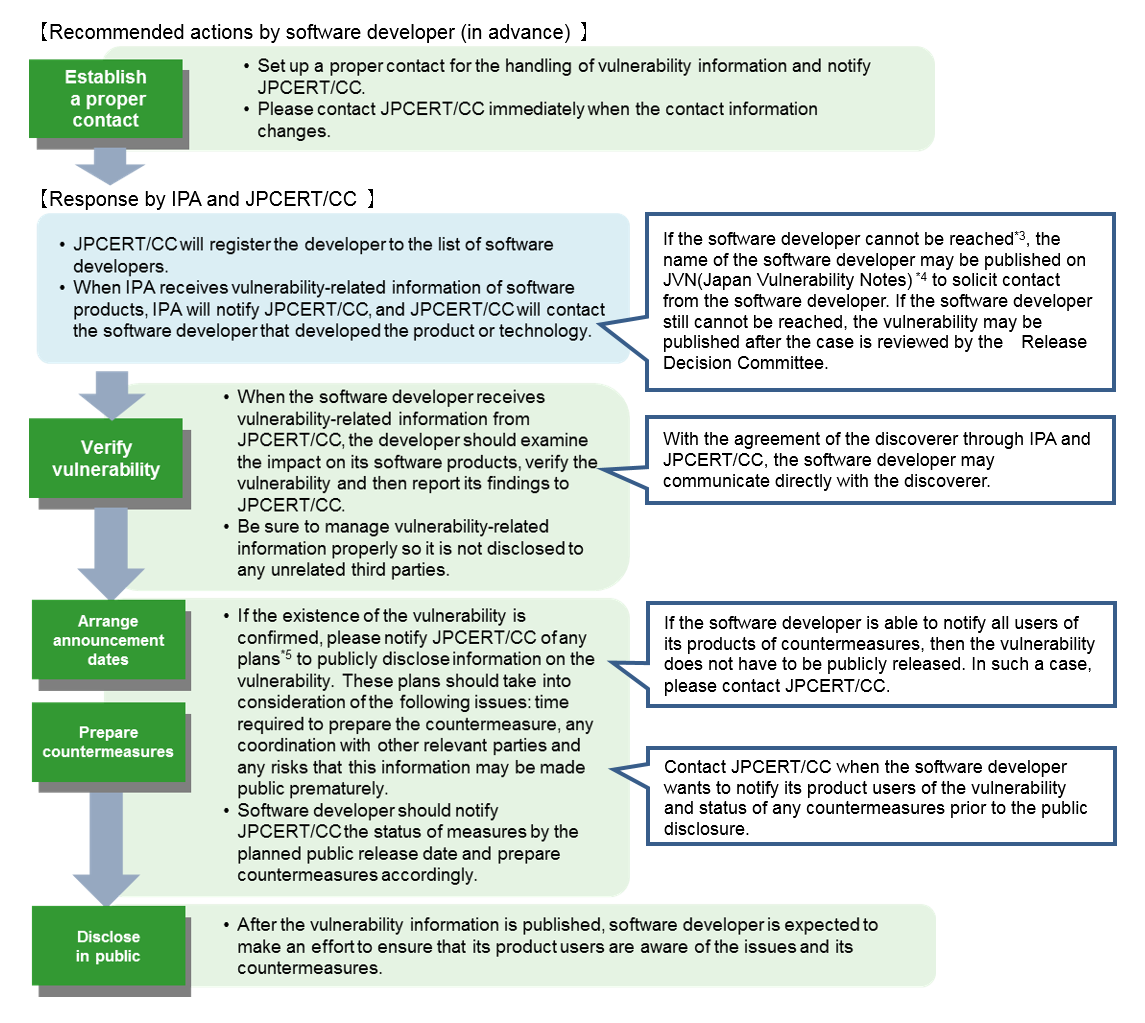
To Software Developers
When software developers*2 are notified that there is a vulnerability in their software product, they are expected to verify the content of the notification. If the vulnerability in question exists, they are expected to make sure users are aware of any available countermeasures. Please cooperate when receiving inquiries from JPCERT/CC on any technical matters and the progress in addressing the vulnerability.
*2) The company or individual that developed the software. If the software is developed abroad, this includes companies with the primary sales rights for that software product in Japan (e.g. Japanese affiliates of foreign companies, sole distributors etc.) . *3) Cases where the developer cannot be reached: contact information for the developer is unknown, an appropriate method to contact the developer does not exist, the developer does not respond to contact attempts, etc.
*4) JVN (Japan Vulnerability Notes): https://jvn.jp/en/
*5) In general, the recommended date of release is 45 days from the day of the initial report. Please contact JPCERT/CC if more time is necessary. For reports that have been handled for over a year, the discoverer may ask IPA to withdraw its request for information non-disclosure. After the request is withdrawn, the vulnerability information may be made public by the discoverer.
- Vulnerability Disclosure Guideline for Software Developers
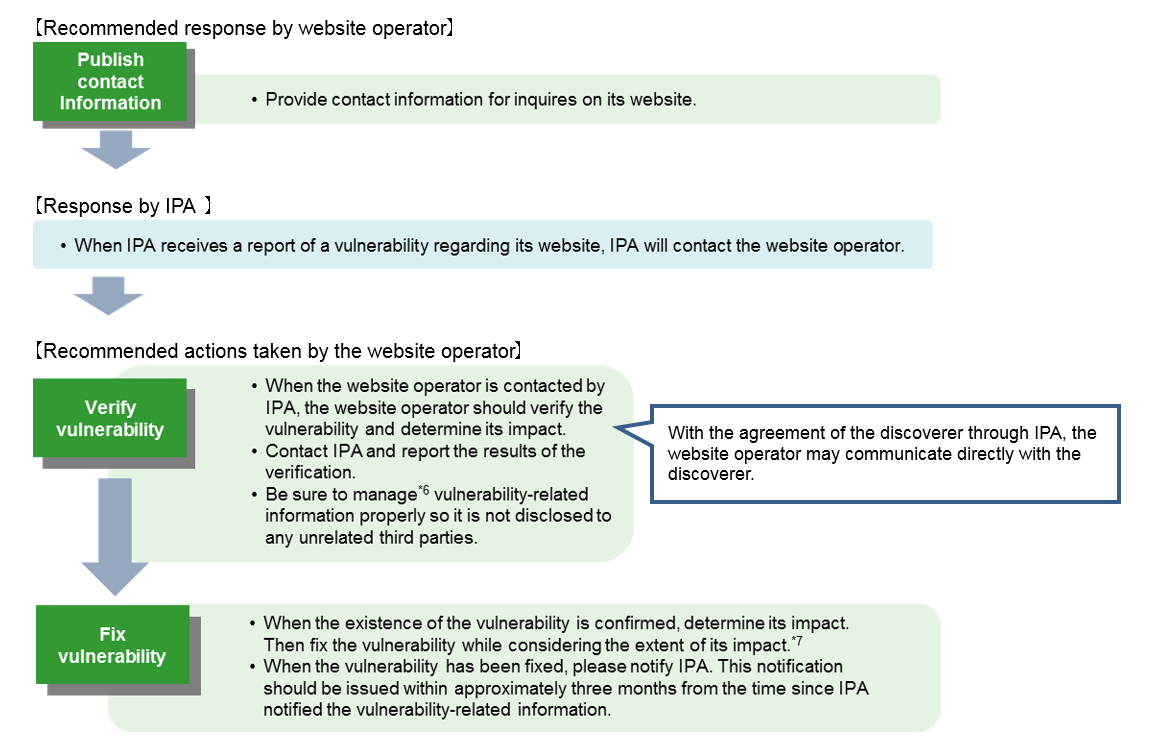
To Website Operators
When website operators are notified of the possibility that a vulnerability exists in their websites, they are expected to verify the notified vulnerability. If the vulnerability exists, they are expected to fix the notified vulnerability while considering the extent of its impact. Please also cooperate when receiving inquiries from IPA on technical matters and the progress in dealing with the vulnerability.
*6) It is recommended that a confidentiality agreement be concluded with companies contracted to build and operate website before communicating vulnerability-related information.
*7) It is not required for website operator to proactively publish vulnerability in website. However, if breach of personal data because of notified vulnerability is suspected, then publishing the vulnerability should be considered to prevent secondary damage to users and other incidents after it has been fixed. Inquiries from any individuals who have been affected by a vulnerability should be responded to in a prompt manner.
- How to Secure Your Web Site
How to Report
If you have discovered a vulnerability and would like to report to IPA, please check the following URL (Japanese only). If it is a software product vulnerability, JPCERT/CC will contact the software developer. If it is a website vulnerability, IPA will contact the website operator.
- Report Vulnerabilities
-
- About Receiving Vulnerability-related Information
- Japanese Only
- About Receiving Vulnerability-related Information
- Reporting Methods and Forms
-
- Contact to report
- Japanese Only
- Contact to report
Inquiries Regarding This Document
If you have any questions, contact the following email address. When you send email, please include “[INQ]” in its subject.
- E-mail:

* Email address above is for inquiries only. If you would like to report about vulnerability-related information check “Contact to Report”.
Other Information
- Public awareness campaign materials
- Japanese Only
- IPA/ISEC:Vulnerabilities:Quarterly Reports