Enhancing information security

Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2022 4th Quarter (Oct. - Dec.)]
Release Date:Feb 22, 2023
IT Security Center
1. 2022 4th Quarter: Vulnerability Countermeasure Information Database JVN iPedia Registration Status
The vulnerability countermeasure information database JVN iPedia is endeavoring to become a comprehensive vulnerability database where vulnerability information is aggregated for easy access for IT users. JVN iPedia collects and/or translates the vulnerability information published by 1) domestic software developers, 2) JVN (footnote 1), a vulnerability information portal run by JPCERT/CC and IPA, and 3) NVD (footnote 2), a vulnerability database run by NIST (footnote 3). JVN iPedia has been making vulnerability information available to the public since April 25, 2007.
1-1. Vulnerabilities Registered in 2022/4Q
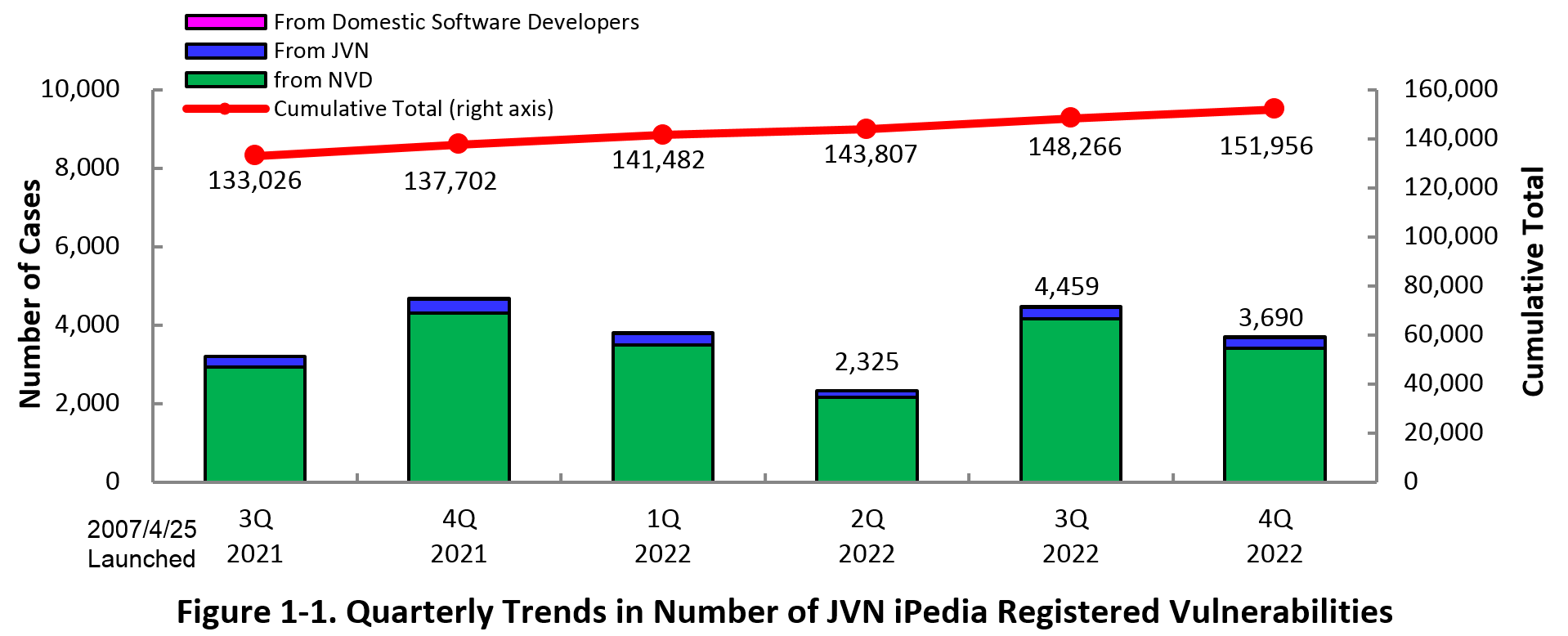
JVN iPedia now stores 151,956 vulnerabilities
The summary of the vulnerability information registered to the Japanese version of JVN iPedia during the 4th quarter of 2022 (October 1 to December 31, 2022) is shown in the table below. As of the end of December 2022, the total number of vulnerabilities stored in JVN iPedia is 151,956 (Table 1-1, Figure 1-1).
As for the JVN iPedia English version, the total number of vulnerabilities stored is 2,527 as shown in the lower half of the Table 1-1.
Table 1-1. Vulnerabilities Registered to JVN iPedia during 4th Quarter of 2022
|
|
Information Source
|
Registered Cases
|
Cumulative Cases
|
|---|---|---|---|
|
Japanese Version
|
Domestic Product Developers
|
2 cases
|
268 cases
|
|
JVN
|
270 cases
|
11,939 cases
|
|
|
NVD
|
3,418 cases
|
139,749 cases
|
|
|
Total
|
3,690 cases
|
151,956 cases
|
|
|
English Version
|
Domestic Product Developers
|
2 cases
|
263 cases
|
|
JVN
|
42 cases
|
2,264 cases
|
|
|
Total
|
44 cases
|
2,527 cases
|
1-2. 【Observation 1】Internet Explorer support ended
Please move to Microsoft Edge due to the end of support for Internet Explorer
On June 16, 2022 (Japan time), support for Internet Explorer, a browser provided by Microsoft, ended(footnote 4). After the end of support, Microsoft Edge launches when you try to use Internet Explorer.
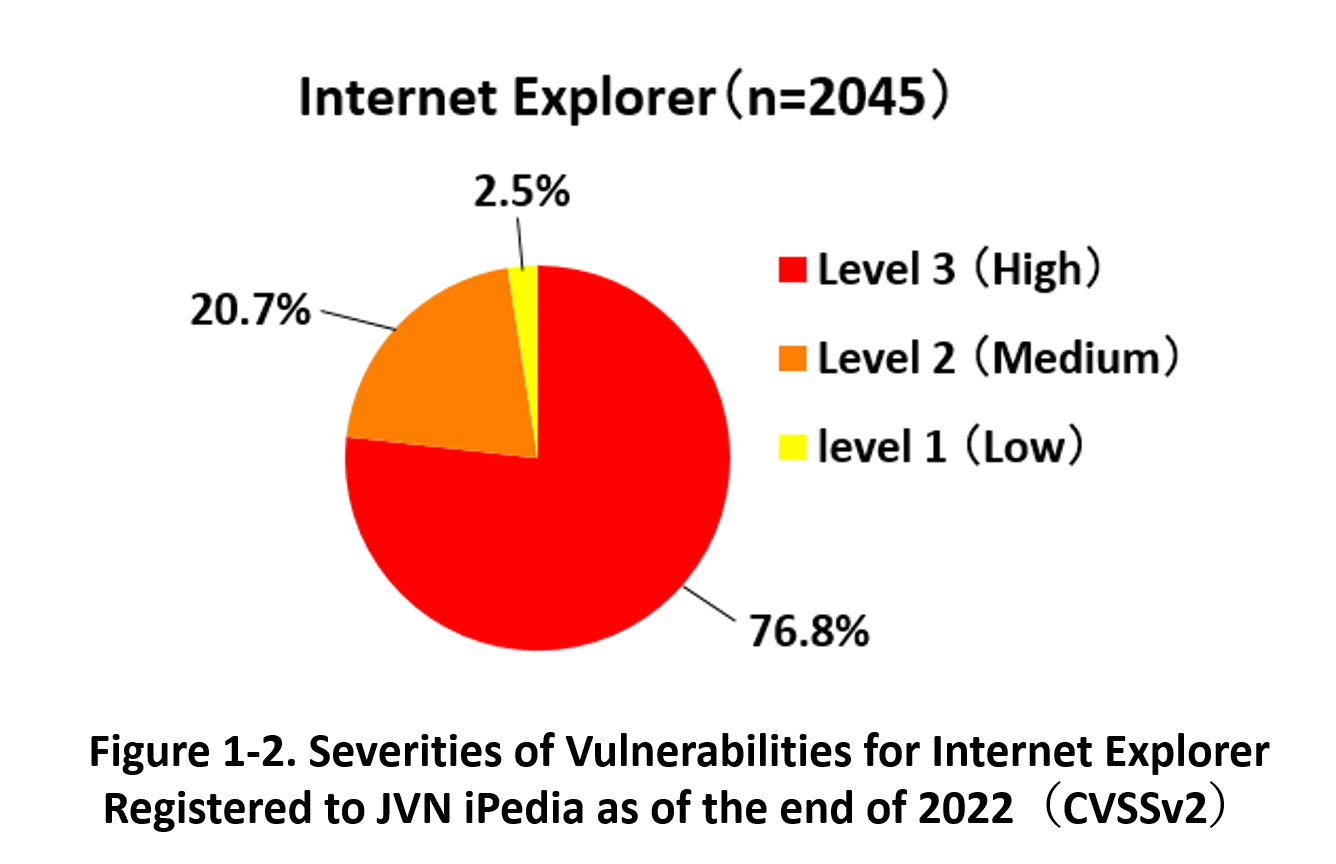
As of the end of December 2022, 2,045 vulnerabilities related to Internet Explorer have registered in JVN iPedia. As for the severity of those vulnerabilities (CVSS v2.0 ratings), the highest severity “High” (CVSS base score=7.0–10.0) is 76.8% for 1,570 vulnerabilities, followed by “Medium” (CVSS base score=4.0–6.9) is 20.7% for 424, and “Low” (CVSS base score=0.1–3.9) is 2.5% for 51.
On the other hand, there was a case where a vulnerability related to Internet Explorer was unintentionally exploited by a hacker group, even though a user used another browser in the wake of the end of support for Internet Explorer. In November 2022, Microsoft disclosed a remote code execution vulnerability in Internet Explorer's JScript engine "jscript9.dll" (CVE-2022-41128). The vulnerability was exploited by a hacker group in a zero-day attack at the end of October before the security update program was released(footnote 5) . Since a word file that exploited the vulnerability was uploaded online, if a viewer opened the file and gave permission to execute a macro, remote code execution via Internet Explorer could be possible. This vulnerability has been fixed by Microsoft's November security update that fixes the Windows OS.
As in this case, if the software not in use exists on a computer, attackers may exploit the vulnerability of the software. For the software which no longer supported, appropriate measures, such as uninstalling, are required. When Microsoft releases security updates addressing the discovered vulnerabilities, users should apply the updates immediately. However, note that the release of security updates is generally limited to "supported" software. Therefore, after the end of support for Internet Explorer in June 2022, even if vulnerabilities are found in the future, Microsoft will not release security updates, and users may not be able to address the vulnerabilities. Although Microsoft released a security update in response to the vulnerability "CVE-2022-41128", this update was released to address the vulnerability in the Windows OS and was not for Internet Explorer, which is no longer supported.
With the end of support for Internet Explorer, Microsoft has made an announcement that recommends users to transit Internet Explorer to Microsoft Edge. Microsoft Edge is Microsoft's supported browser, the successor to Internet Explorer, and has been a standard feature since Windows 10. Although it will only be available until 2029, it has an "IE mode" that is compatible with Internet Explorer and can view in the same way, so when you want to browse websites that only work with Internet Explorer, you can browse those sites by switching the mode.
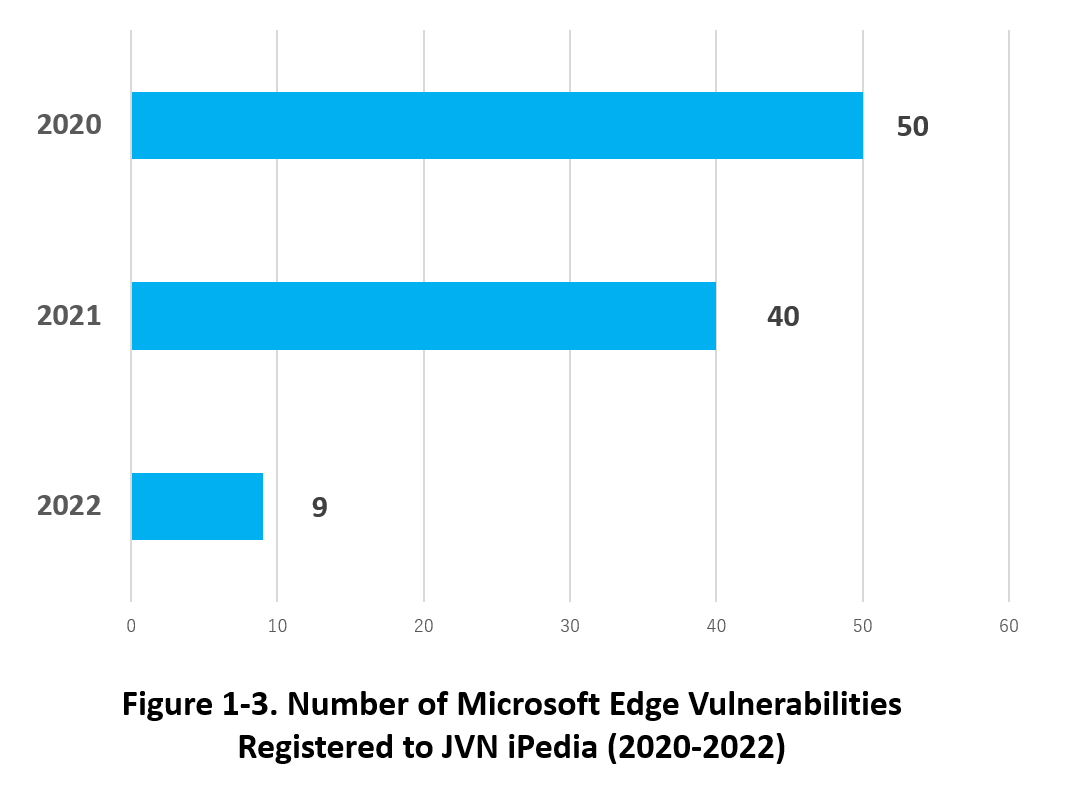
For Microsoft Edge, many vulnerabilities have also been disclosed since its release in 2015. Figure 1-3 shows the number of Microsoft Edge vulnerabilities registered to JVN iPedia in the last three years (2020-2022) by year. Although the number of registered vulnerabilities in JVN iPedia is decreasing, we recommend regularly applying security updates released by Microsoft because vulnerability discovery is unpredictable.
IPA releases emergency countermeasure information when a severe vulnerability attack occurs. In addition, IPA provides a cyber security alert service called "icat for JSON(footnote 6)" to receive the information as soon as possible. Please utilize these services.
1-3. 【Observation 2】Attacks using known vulnerabilities related to Microsoft Exchange Server
Be sure to perform regular updates correctly. Make sure you have not missed any updates.
In the November 2022 Security Update, Microsoft disclosed vulnerabilities that confirmed exploitation in targeted attacks. Targeted attacks have ranked high in recent years on IPA's annual list "10 Major Security Threats 2022" (ranked second as "Confidential Information Theft by APT" in "10 Major Security Threats 2022 [For Organizations]"). Exploited vulnerabilities in targeted attacks were ‘Microsoft Exchange Server Elevation of Privilege Vulnerability’ (CVE-2022–41040) (footnote 7) and ‘Microsoft Exchange Server Remote Code Execution Vulnerability’ (CVE-2022–41082) (footnote 8), which together could allow an attacker to steal permissions and remotely execute arbitrary code. The pair of vulnerabilities is dubbed "ProxyNotShell." Both vulnerabilities had a CVSSv3 score of 8.8, which is the second highest severity ‘High’ (CVSSv3 base score 7.0-8.9).
Although attacks exploiting "ProxyNotShell" decreased after the release of the security update, new attacks using a combination of CVE-2022-41080 and CVE-2022-41082 to circumvent the "ProxyNotShell" mitigation have been executing since late November 2022. CVE-2022-41080 (footnote 9)'Microsoft Exchange Server Elevation of Privilege Vulnerability' is similar to CVE-2022–41040. Those attacks were remote code executions by illegally stealing privileges through the "Outlook Web Access (OWA)" system associated with Exchange Server. This attack method is called "OWASSRF". CVE-2022-41080, like CVE-2022-41040 and CVE-2022-41082, was a vulnerability fixed in the November 2022 Security Update. However, attackers targeted users who had not applied the update to their systems.
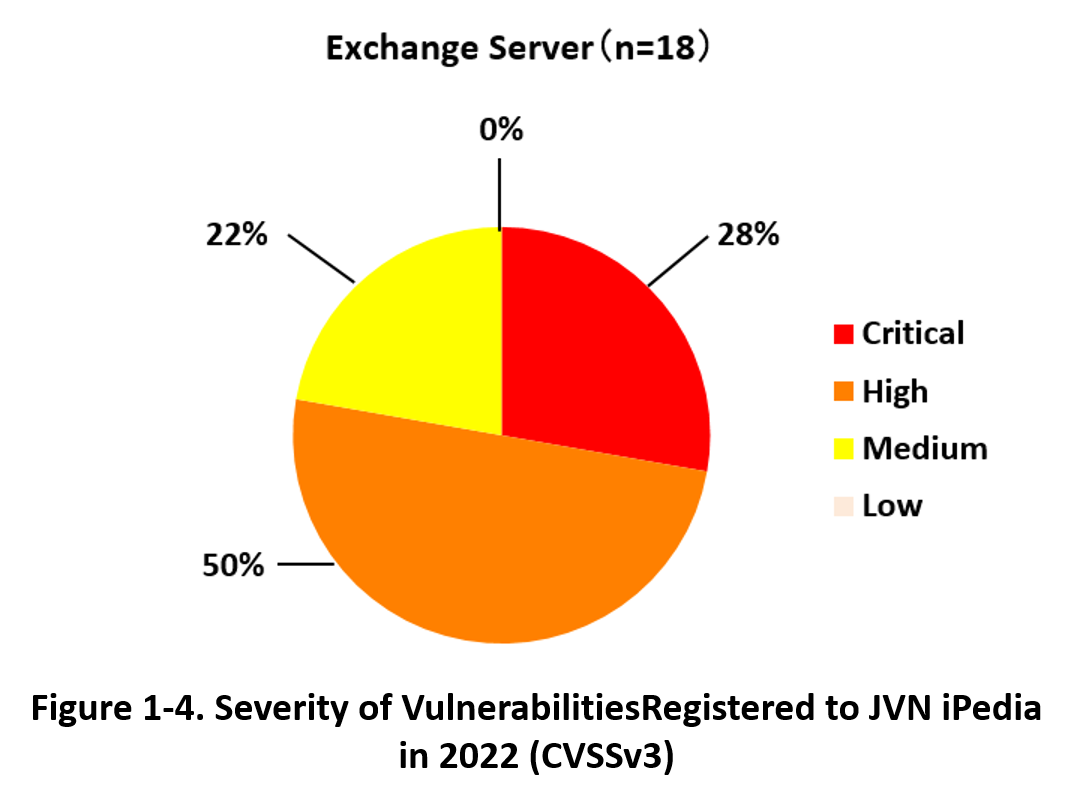
Figure 1-4 shows the percentage of the severity of vulnerabilities of Exchange Server registered to JVN iPedia in 2022.
The number of registered vulnerabilities of Exchange Server in 2022 was 18, of which 27.8% was the highest severity 'Critical' (CVSSv3 base score=9.0–10.0), and 50.0 % was the second highest severity 'High' (CVSSv3 base score=7.0–8.9). This data indicates a trend that requires immediate action in the event of a vulnerability.
Since the "ProxyNotShell" was a zero-day vulnerability exploited before the security update was released, taking countermeasures in advance was difficult for organizations. However, applying the update after the release prevented subsequent damages. When it comes to "OWASSRF", it was preventable if organizations applied the security update regularly. Regardless of the presence or absence of zero-day attacks, applying security updates or patches soon after the release is highly recommended to avoid being victimized. When you can't apply updates to your system for some reason, please consider using a workaround or other alternative solution. Please check the rules for your organization's system once again.
2. Details on JVN iPedia Registered Data
2-1. Types of Vulnerabilities Reported
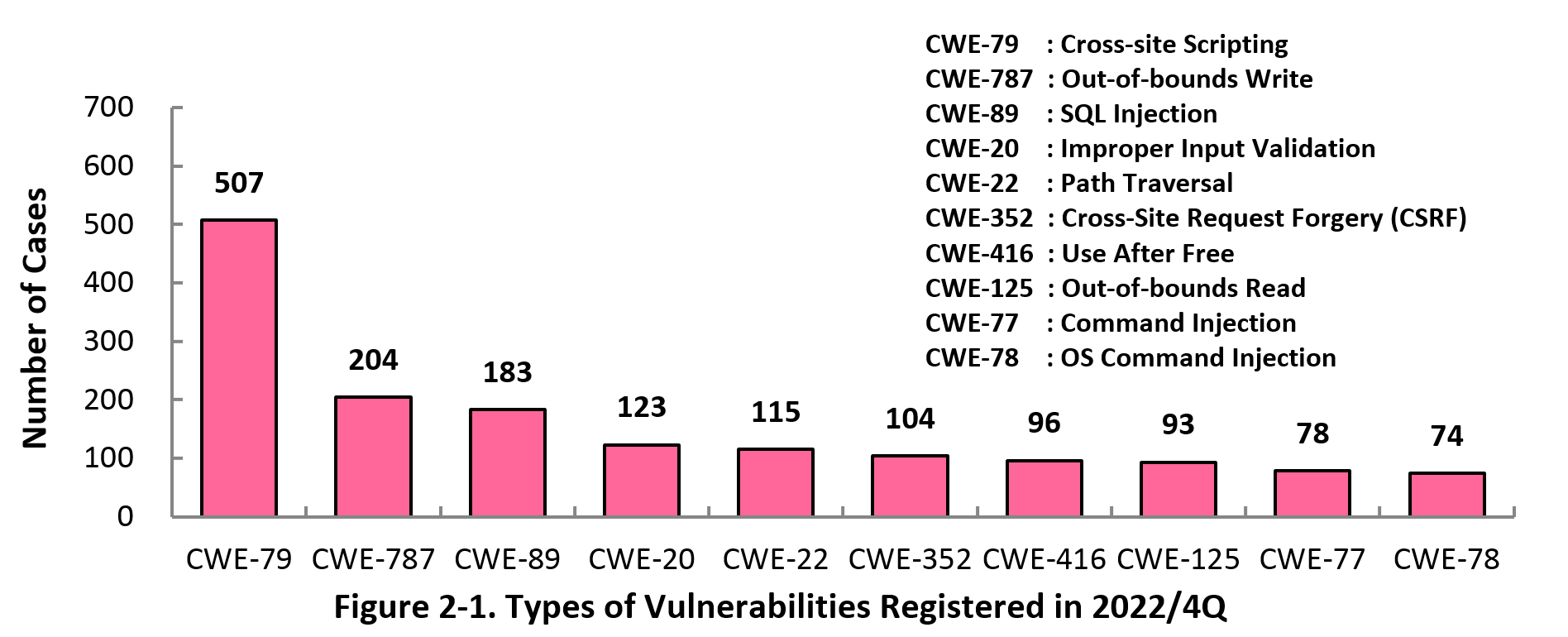
Figure 2-1 shows the number of vulnerabilities newly added to JVN iPedia during the 4th quarter of 2022, sorted by the CWE vulnerability types.
The type of the vulnerabilities reported most in the 4th quarter is CWE-79 (Cross-Site Scripting) with 507 cases, followed by CWE-787 (Out-of-bounds Write) with 204, CWE-89 (SQL Injection) with 183, CWE-20 (Improper Input Validation) with 123, CWE-22 (Path Traversal) with 115.
CWE-79 (Cross-site Scripting), the most reported vulnerability type in this quarter, could allow attackers to display false webpages and/or steal information.
Software developers need to make sure to mitigate vulnerability from the planning and design phase of software development. IPA provides tools and guidelines, such as "Vulnerability Countermeasure Guide for Software Developers"" (footnote 10), "How to Secure Your Website" (footnote 11), "Secure Programming Guide" (footnote 12) and "AppGoat" (footnote 13), a hands-on venerability learning tool, for website developers and operators to build secure websites.
2-2. Severity of Vulnerabilities Reported
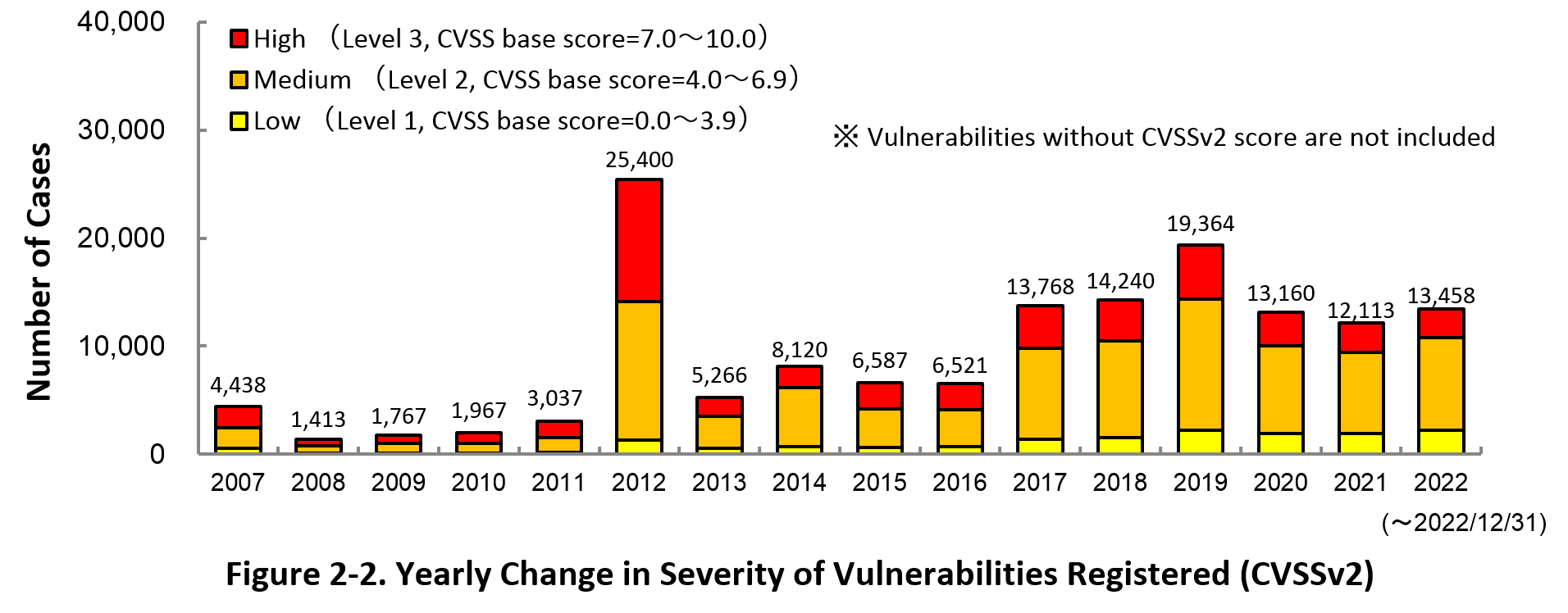
Figure 2-2 shows the yearly change in the CVSSv2 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2022, 19.8% are “Level III” (7.0 - 10.0), 64.0% are “Level ll” (4.0 – 6.9) and 16.2% are “Level I” (0.0 – 3.9). This means 83.8% of all vulnerabilities registered are Level II or higher, which are potentially critical enough to cause damage like information exposure or data falsification.
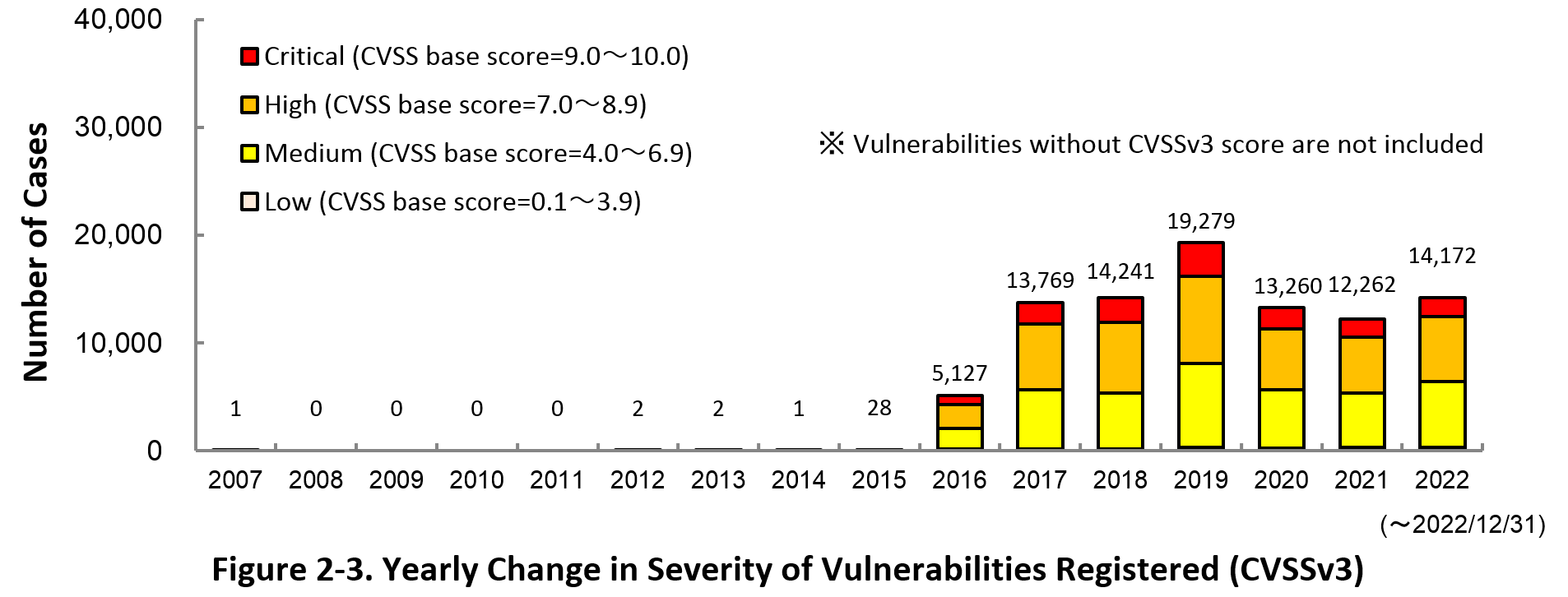
Figure 2-3 shows the yearly change in the CVSSv3 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2022, 12.3% are “Critical” (9.0 – 10.0), 42.2% are “High” (7.0 – 8.9), 43.3% are “Medium” (4.0 – 6.9) and 2.3% are “Low” (0.1 – 3.9).
To avoid threats posed by the known vulnerabilities, both product developers and IT users should pay close attention to vulnerability disclosure and update software they use to a fixed version or apply a security patch as soon as possible when they become available. IT users can check vulnerabilities newly published on JVN iPedia in RSS and XML format (footnote 14) as well.
2-3. Types of Software Reported with Vulnerability
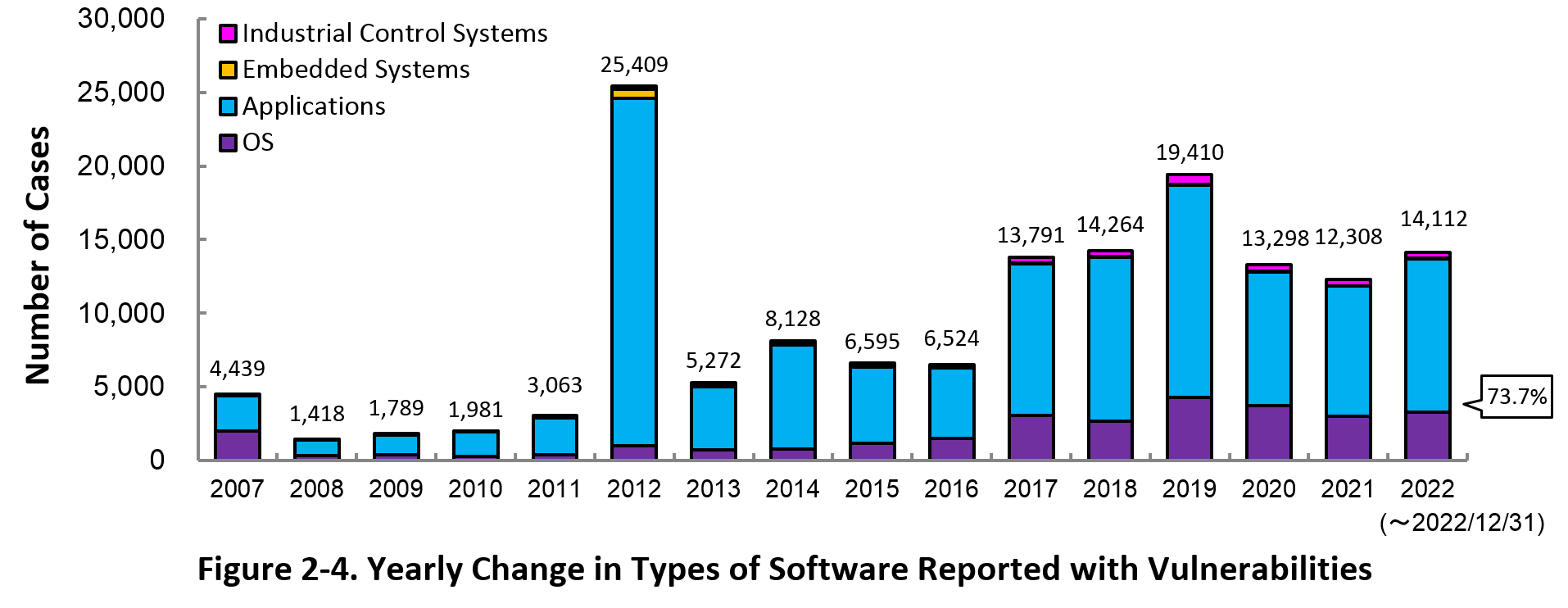
Figure 2-4 shows the yearly change in the type of software reported with vulnerability. Application vulnerabilities have been published most, accounting for 73.7% (117,951 out of 151,801) of the 2022 total.
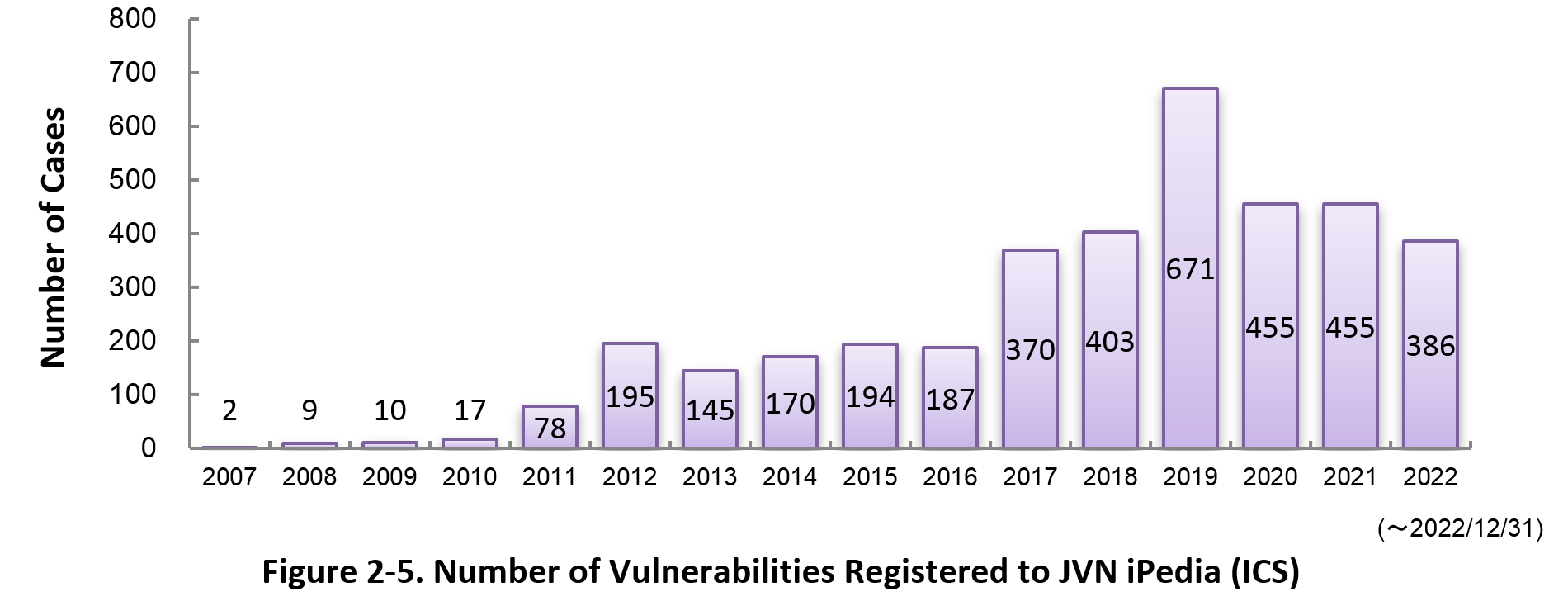
Figure 2-5 shows the yearly change in the number of JVN iPedia-stored vulnerabilities in industrial control systems (ICS) used in critical infrastructure sectors. As of December 2022, the total of 3,747 ICS vulnerabilities have been registered.
2-4. Products Reported with Vulnerability
Table 2-1 lists the top 20 software whose vulnerabilities were most registered to JVN iPedia during the 4th quarter (October to December) of 2022.
In this quarter, the most registered products were Google Android OS products. After the second place, many Qualcomm and Windows OS products, which continued from the previous quarter, were on the list.
Besides those in the top 20 list, JVN iPedia stores and offers vulnerability information about a variety of software. IPA hopes software developers and users will make good use of JVN iPedia to efficiently check vulnerability information and take necessary action in a timely manner (footnote 15).
Table 2-1. Top 20 most registered software products vulnerability countermeasure information in JVN iPedia [Oct. – Dec. 2022]
|
Rank
|
Category
|
Product Name (Vendor)
|
Number of
Vulnerabilities Registered |
|---|---|---|---|
|
1
|
OS
|
Android (Google)
|
186
|
|
2
|
Firmware
|
Qualcomm component (Qualcomm)
|
180
|
|
3
|
OS
|
Debian GNU/Linux (Debian)
|
164
|
|
4
|
OS
|
Fedora (Fedora Project)
|
163
|
|
5
|
OS
|
Microsoft Windows Server 2022 (Microsoft)
|
129
|
|
5
|
OS
|
Microsoft Windows 11 (Microsoft)
|
129
|
|
7
|
OS
|
Microsoft Windows 10 (Microsoft)
|
128
|
|
8
|
OS
|
Microsoft Windows Server 2019 (Microsoft)
|
123
|
|
9
|
OS
|
Microsoft Windows Server 2016 (Microsoft)
|
107
|
|
10
|
OS
|
HarmonyOS (Huawei)
|
102
|
|
11
|
OS
|
Microsoft Windows Server 2012 (Microsoft)
|
94
|
|
12
|
OS
|
Microsoft Windows 8.1 (Microsoft)
|
91
|
|
13
|
OS
|
Microsoft Windows RT 8.1 (Microsoft)
|
88
|
|
14
|
OS
|
Microsoft Windows Server 2008 (Microsoft)
|
82
|
|
15
|
OS
|
Microsoft Windows 7 (Microsoft)
|
78
|
|
16
|
Others
|
Magic UI (Huawei)
|
72
|
|
16
|
Others
|
EMUI (Huawei)
|
72
|
|
18
|
Browser
|
Google Chrome (Google)
|
67
|
|
19
|
Firmware
|
RBR850 Firmware (Netgear)
|
49
|
|
19
|
Firmware
|
RBK852 Firmware (Netgear)
|
49
|
3. Most Accessed Vulnerability Countermeasure Information
Table 3-1 lists the top 20 most accessed vulnerability countermeasure information in JVN iPedia during the 4th quarter of 2022 (October to December).
This quarter, 11 out of 20 vulnerabilities were vulnerabilities in WordPress or WordPress plugins. Compared to the previous quarter, the number of vulnerabilities in OS products decreased.
Rating Scale
Note 1) CVSSv2 Severity Rating Scale
- Level I (Low)
- CVSS Base Score = 0.0~3.9
- Level II (Medium)
- CVSS Base Score = 4.0~6.9
- Level III (High)
- CVSS Base Score = 7.0~10.0
Note 2) CVSSv3 Severity Rating Scale
- Low
- CVSS Base Score =0.1~3.9
- Medium
- CVSS Base Score =4.0~6.9
- High
- CVSS Base Score =7.0~8.9
- Critical
- CVSS Base Score =9.0~10.0
Table 3-1. Top 20 Most Accessed Vulnerability Countermeasure Information in JVN iPedia [Oct. – Dec. 2022]
No.1 XMP Toolkit SDK vulnerable to classic buffer overflow JVNDB-2021-012563
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
- High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2022/9/2
- Access Count
-
9,419
No.2 Use-after-free vulnerability in multiple Apple products (in Japanese only) JVNDB-2021-013508
- CVSSv2 Severity Rating Scale
-
- Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2022/9/14
- Access Count
-
8,100
No.3 WordPress plugin “Shopp” vulnerable to unrestricted upload of files with dangerous type (in Japanese only) JVNDB-2021-012173
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2022/8/25
- Access Count
-
6,638
No.4 Improper access control vulnerability in Rancher JVNDB-2021-012490
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.9
- Date Public
-
2022/9/1
- Access Count
-
6,135
No.5 Multiple vulnerabilities in Buffalo network devices JVNDB-2022-002444
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
8.8
- Date Public
-
2022/10/5
- Access Count
-
5,569
No.6 Growi vulnerable to improper access control JVNDB-2022-000076
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
- Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2022/10/7
- Access Count
-
5,485
No.7 Multiple vulnerabilities in nadesiko3 JVNDB-2022-000082
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2022/10/20
- Access Count
-
5,481
No.8 Multiple vulnerabilities in WordPress JVNDB-2022-000087
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.3
- Date Public
-
2022/11/8
- Access Count
-
5,330
No.9 WordPress Plugin "Advanced Custom Fields" vulnerable to missing authorization JVNDB-2022-000023
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.5
- Date Public
-
2022/3/30
- Access Count
-
4,906
No.10 WordPress Plugin "Newsletter" vulnerable to cross-site scripting JVNDB-2022-000057
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2022/7/25
- Access Count
-
4,862
No.11 WordPress plugin "WP Statistics" vulnerable to cross-site scripting JVNDB-2022-000038
- CVSSv2 Severity Rating Scale
-
- Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
- Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2022/5/24
- Access Count
-
4,795
No.12 WordPress Plugin "Modern Events Calendar Lite" vulnerable to cross-site scripting JVNDB-2022-000041
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.4
- Date Public
-
2022/6/1
- Access Count
-
4,756
No.12 WordPress Plugin "MicroPayments - Paid Author Subscriptions, Content, Downloads, Membership" vulnerable to cross-site request forgery JVNDB-2022-000026
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2022/4/15
- Access Count
-
4,752
No.14 Race condition vulnerability in Apache Tomcat JVNDB-2022-002436
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.3
- Date Public
-
2022/10/3
- Access Count
-
4,659
No.15 Apache Tomcat vulnerable to HTTP request smuggling JVNDB-2022-002639
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2022/11/4
- Access Count
-
4,640
No.16 Multiple vulnerabilities in WordPress Plugin "Quiz And Survey Master" JVNDB-2022-000002
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
- Medium
- CVSSv3 Base Score
-
5.4
- Date Public
-
2022/1/12
- Access Count
-
4,634
No.17 Multiple missing authorization vulnerabilities in WordPress Plugin "Advanced Custom Fields" JVNDB-2021-000109
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/12/2
- Access Count
-
4,600
No.18 IPFire WebUI vulnerable to cross-site scripting JVNDB-2022-000075
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.8
- Date Public
-
2022/10/6
- Access Count
-
4,592
No.19 WordPress Plugin "Push Notifications for WordPress (Lite)" vulnerable to cross-site request forgery JVNDB-2021-000103
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/11/16
- Access Count
-
4,574
No.19 WordPress Plugin "OG Tags" vulnerable to cross-site request forgery JVNDB-2021-000086
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/9/28
- Access Count
-
4,574
Table 3-2 lists the top 5 most accessed vulnerability information among those reported by domestic product developers.
Table 3-2. Top 5 Most Accessed Vulnerabilities Reported by Domestic Product Developers [Oct. - Dec. 2022]
No.1 Privilege Escalation Vulnerability in Hitachi Storage Plug-in for VMware vCenter JVNDB-2022-002443
- CVSSv2 Base Score
-
- -
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
- 5.4
- Date Public
-
2022/10/5
- Access Count
-
4,372
No.2 DoS Vulnerability in uCosminexus TP1/Client/J and Cosminexus Service Coordinator JVNDB-2022-002364
- CVSSv2 Base Score
-
- -
- CVSSv3 Base Score
-
-
- Date Public
-
2022/9/14
- Access Count
-
3,190
No.3 Information Disclosure Vulnerability in Hitachi Automation Director and Hitachi Ops Center Automator JVNDB-2022-002143
- Information Disclosure Vulnerability in Hitachi Automation Director and Hitachi Ops Center Automator
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2022/8/1
- Access Count
-
2,698
No.4 File Permission Vulnerability in Hitachi Command Suite JVNDB-2022-001382
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2022/3/7
- Access Count
-
2,639
No.5 Cross-site Scripting Vulnerability in JP1/IT Desktop Management 2 JVNDB-2022-001299
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2022/2/8
- Access Count
-
2,625
Footnotes
(1) Japan Vulnerability Notes: A portal for vulnerability countermeasure information including information on vendor response to the reported vulnerabilities and security support. Operated in the collaboration of IPA and JPCERT/CC.
(2) National Vulnerability Database: A vulnerability database operated by NIST.
(3) National Institute of Standards and Technology: A U.S federal agency that develops and promotes measurement, standards and technology.
(4) The future of Internet Explorer on Windows 10 is in Microsoft Edge
(5) Google Explains Attack from North Korea Targeting South Korean Users by Exploiting Zero-Day Vulnerability in IE (in Japanese only)
(6) IPA Cyber Security Alert Service "icat for JSON" (in Japanese only)
(7) JVNDB-2022-002439 - Improper Privilege Management Vulnerability in Microsoft Exchange Server (in Japanese only)
(8) JVNDB-2022-002438 - Vulnerability in Microsoft Exchange Server (in Japanese only)
(9) JVNDB-2022-002733 - Elevation of Privilege Vulnerability in Microsoft Exchange Server (in Japanese only)
(10) Vulnerability Countermeasure Guide for Software Developers (in Japanese only)
(11) How to Secure Your Websites (latest version in Japanese only)
(12) Secure Programming Guide (in Japanese only)
(13) AppGoat (in Japanese only)
(14) IPA Data Feeds (in Japanese only)
(15) IPA Technical Watch - Daily Practice Guide (in Japanese only): Tips on Vulnerability Management The guide gives tips on how to efficiently and efficiently collect and leverage vulnerability information.
Past Quarterly Reports
Contact information
IT Security Center,
Information-technology Promotion Agency, Japan (ISEC/IPA)