Enhancing information security

Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2018 4th Quarter (Oct. - Dec.)]
Release Date:Feb 21, 2019
IT Security Center
1. 2018 4th Quarter: Vulnerability Countermeasure Information Database JVN iPedia Registration Status
The vulnerability countermeasure information database JVN iPedia (https://jvndb.jvn.jp/en/) is endeavoring to become a comprehensive vulnerability database where vulnerability information is aggregated for easy access for IT users. JVN iPedia collects and/or translates the vulnerability information published by 1) domestic software developers, 2) JVN (*1), a vulnerability information portal site run by IPA and JPCERT/CC, and 3) NVD (*2), a vulnerability database run by NIST (*3). JVN iPedia has been making vulnerability information available to the public since April 25, 2007.
1-1. Vulnerabilities Registered in 2018/4Q
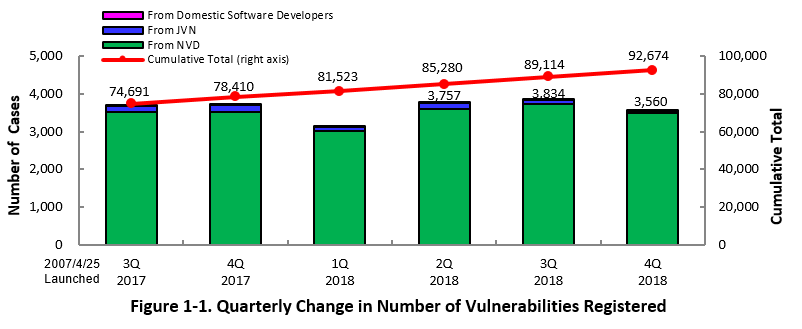
~ JVN iPedia now stores 92,674 vulnerabilities ~
The summary of the vulnerability information registered to the Japanese version of JVN iPedia during the 4th quarter of 2018 (October 1 to December 31, 2018) is shown in the table below. As of the end of December 2018, the total number of vulnerabilities stored in JVN iPedia is 92,674 (Table 1-1, Figure 1-1).
As for the English version, the total of 1,997 vulnerabilities are available as shown in the lower half of the table.
Table 1-1. Registered Vulnerabilities in 4th Quarter of 2018
|
|
Information Source
|
Registered Cases
|
Cumulative Cases
|
|---|---|---|---|
|
Japanese Version
|
Domestic Product Developers
|
6 cases
|
210 cases
|
|
JVN
|
66 cases
|
8,271 cases
|
|
|
NVD
|
3,488 cases
|
84,193 cases
|
|
|
Total
|
3,560 cases
|
92,674 cases
|
|
|
English Version
|
Domestic Product Developers
|
6 cases
|
210 cases
|
|
JVN
|
36 cases
|
1,787 cases
|
|
|
Total
|
42 cases
|
1,997 cases
|
1-2. Hot Topic #1: Java SE Vulnerabilities
~ Free public updates for Java SE 8, a version identified with lots of relatively severe vulnerabilities, now ended ~
Java SE developer Oracle Corporation announced that free public updates for Java SE 8 (Java Platform, Standard Edition 8) would not be available for business, commercial or production use (without a commercial license) after January 2019 (*4). If continuing to use the software without vendor support, since patches are no longer available even if new vulnerabilities are found, there would be quite a possibility where undesired consequences, such as information exposure and/or unexpected service disruption, may occur when unfixed vulnerabilities are exploded by attackers. Because Java SE is widely used by many organizations and the impact of successful attacks could be huge, IPA released a security alert for the Java SE 8 end-of-life issue (*5).
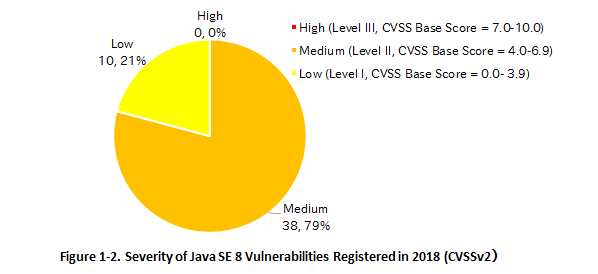
Figure 1-2 shows the severity of Java SE 8 vulnerabilities registered to JVN iPedia in the past year, from January 1 to December 31, 2018. There were no severest "Level III" vulnerabilities (CVSS Base Score = 7.0 – 10.0), but nearly 80 percent, 38 out of 48, were relatively severe "Level II" vulnerabilities (CVSS Base Score = 4.0 – 6.9). In case a similar number and level of vulnerabilities are discovered and disclosed in the coming years, commercial users who plan to continue to use Java SE 8 need to take some steps, such as using a paid support service, to protect their systems from attacks that exploit vulnerabilities.
1-3. Hot Topic #2: Types of Vulnerabilities Registered to JVN iPedia
~ Cross-site scripting and buffer errors top the list - a continuous trend from the previous year. Integer overflow found in hundreds of tokens jumped sharply ~
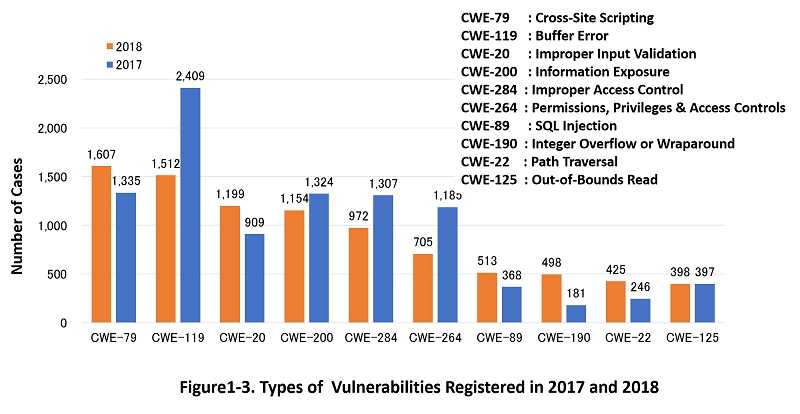
Figure 1-3 shows top 10 CWE types of vulnerabilities registered to JVN iPedia in 2018, and their number is compared to that of 2017.
In 2018, ranked 1st is CWE-79 (Cross-Site Scripting) and 2nd is CWE-119 (Buffer Errors). They were also top two in the previous year. CWE-119 decreased dramatically compared to 2017, bringing it down to the 2nd place. That is because of a big decrease in the disclosure of vulnerabilities classified as CWE-119 on NVD, a main vulnerability information resource of JVN iPedia. Ranked 3rd is CWE-20 (Improper Input Validation), followed by CWE-200 (Information Exposure) and CWE-284 (Improper Access Control). These top five CWE types account for about 50 percent of all types in 2018.
One of the characteristic vulnerabilities disclosed in 2018 can be the 8th-listed CWE-190 (Integer Overflow or Wraparound). It was 181 in 2017 but more than doubled to 498 in 2018. One factor is that hundreds of tokens compliant to ERC20 (*6), the token standard for Ethereum (*7), were found to have a CWE-190 vulnerability. If exploited, the vulnerability could allow attackers to exchange fraudulently-generated tokens for virtual currencies, making it possible to manipulate their price. As a countermeasure, multiple virtual currency exchanges suspended ERC20 token trading (*8).
2. Details on JVN iPedia Registered Data
2-1. Types of Vulnerabilities Reported
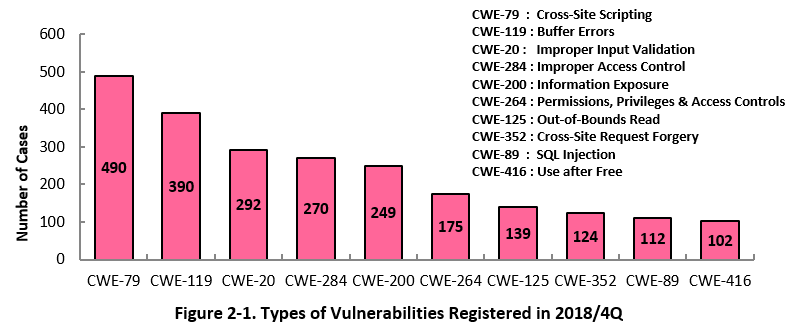
Figure 2-1 shows the number of vulnerabilities newly added to JVN iPedia during the 4th quarter of 2018, sorted by the CWE vulnerability types.
The type of the vulnerabilities reported most in the 4th quarter is CWE-79 (Cross-Site Scripting) with 490 cases, followed by CWE-119 (Buffer Errors) with 390, CWE-20 (Improper Input Validation) with 292, CWE-284 (Improper Access Control) with 270 and CWE-200 (Information Exposure) with 249.
CWE-79, the most reported vulnerability type this quarter, could allow attackers to display false webpages and/or steal information.
Software developers need to make sure to mitigate vulnerability from the planning and design phase of software development. IPA provides tools and guidelines, such as "How to Secure Your Website" (*9), "Secure Programing Guide" (*10) and "AppGoat" (*11), a hands-on venerability learning tool, for website developers and operators to build secure websites.
2-2. Severity of Vulnerabilities Reported
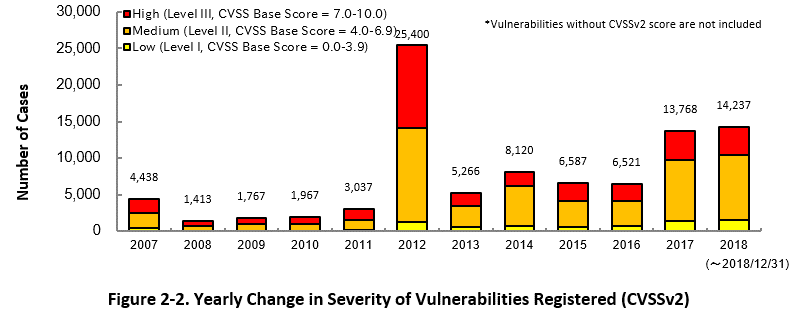
Figure 2-2 shows the yearly change in the CVSSv2 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2018, 26.5 percent are "Level III", 63.0 percent are "Level ll" and 10.5 percent are "Level I". This means 89.5 percent of all vulnerabilities registered are Level II or higher, which are potentially critical enough to cause damage like information exposure or data modification.
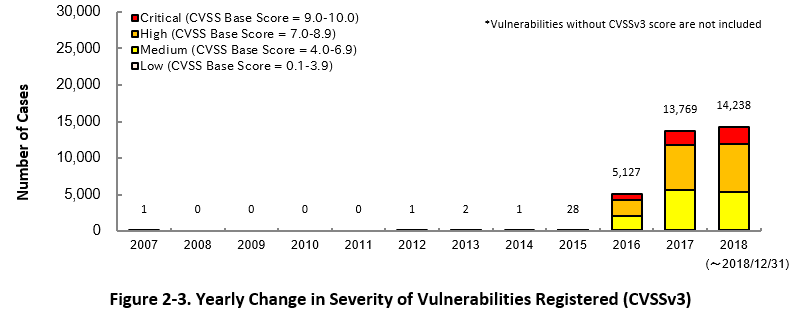
Figure 2-3 shows the yearly change in the CVSSv3 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2018, 16.0 percent are "Critical", 46.3 percent are "High", 36.6 percent are "Medium" and 1.1 percent are “Low”.
To mitigate threats imposed by the known vulnerabilities, both developers and IT users should pay close attention to vulnerability disclosure and update software they are using to a fixed version or apply security patch as soon as they become available. They can also check vulnerabilities newly published on JVN iPeia in RSS and XML format (*12) as well.
2-3. Types of Software Reported with Vulnerability
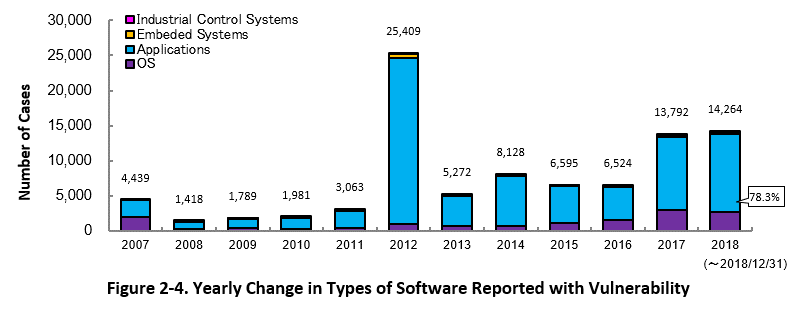
Figure 2-4 shows the yearly change in the types of software reported with vulnerability. Application vulnerabilities have been published most, accounting for 78.3 percent (11,164 out of 14,264) of the 2018 total.
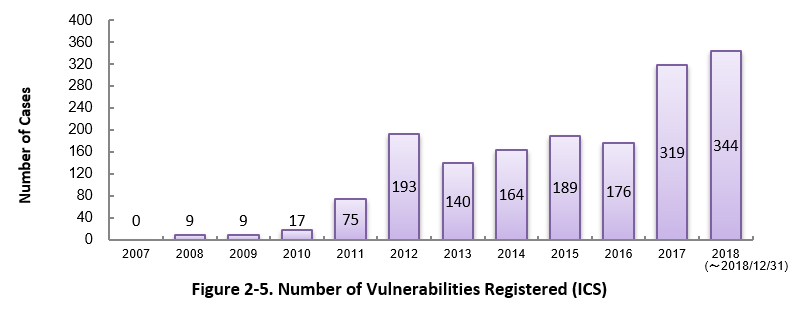
Figure 2-5 shows the yearly change in the number of JVN iPedia-stored vulnerabilities in industrial control systems (ICS) used in critical infrastructure sectors. As of December 2018, the total of 1,635 ICS vulnerabilities have been registered.
3. Products Reported with Vulnerability
Table 2-1 lists the top 20 software whose vulnerabilities were most registered to JVN iPedia during the 4th quarter (October to December) of 2018.
In this quarter, ranked 1st is Debian GNU/Linux. It was also ranked 1st in 2018/1Q (117 vulnerabilities), 3rd in 2Q (171) and 2nd in 3Q (212), meaning that many vulnerabilities have been constantly reported. As a matter of fact, in this quarter, various OS products of popular vendors like Red Hat and Microsoft occupied most of the list.
Besides those in the top 20 list, JVN iPedia stores and offers vulnerability information about a variety of software. IPA hopes software developers and users will make good use of JVN iPedia to efficiently check vulnerability information and take necessary action in a timely manner (*13).
Table 2-1. Top 20 Software Products Vulnerabilities Were Most Registered [Oct. – Dec. 2018]
|
Rank
|
Category
|
Product Name (Vendor)
|
Number of
Vulnerabilities Registered |
|---|---|---|---|
|
1
|
OS
|
Debian GNU/Linux (Debian)
|
177
|
|
2
|
PDF Viewer
|
Foxit Reader (Foxit Software Inc)
|
122
|
|
3
|
PDF Viewer/Editor
|
Foxit PhantomPDF (Foxit Software Inc)
|
121
|
|
4
|
OS
|
Ubuntu (Canonical)
|
108
|
|
5
|
PDF Viewer/Editor
|
Adobe Acrobat (Adobe Systems)
|
95
|
|
5
|
PDF Viewer
|
Adobe Acrobat Reader DC (Adobe Systems)
|
95
|
|
5
|
PDF Viewer/Editor
|
Adobe Acrobat DC (Adobe Systems)
|
95
|
|
8
|
OS
|
Microsoft Windows 10 (Microsoft)
|
90
|
|
9
|
OS
|
Microsoft Windows Server (Microsoft)
|
86
|
|
10
|
OS
|
Microsoft Windows Server 2016 (Microsoft)
|
75
|
|
10
|
OS
|
Android (Google)
|
75
|
|
12
|
OS
|
Red Hat Enterprise Linux Server (Red Hat)
|
68
|
|
13
|
OS
|
Red Hat Enterprise Linux Desktop (Red Hat)
|
59
|
|
13
|
OS
|
Microsoft Windows Server 2012 (Microsoft)
|
59
|
|
13
|
OS
|
Red Hat Enterprise Linux Workstation (Red Hat)
|
59
|
|
16
|
OS
|
Microsoft Windows 8.1 (Microsoft)
|
57
|
|
17
|
OS
|
Microsoft Windows RT 8.1 (Microsoft)
|
56
|
|
18
|
OS
|
Microsoft Windows Server 2008 (Microsoft)
|
55
|
|
19
|
OS
|
Microsoft Windows 7 (Microsoft)
|
53
|
|
20
|
OS
|
Microsoft Edge (Microsoft)
|
50
|
3. Most Accessed Vulnerability Countermeasure Information
Table 3-1 lists the top 20 most accessed vulnerability information in JVN iPedia during the 4th quarter of 2018 (October – December).
Top vulnerability of this quarter is that of FileZen. Its access count is way far more than others’ but it is due to a fact that there were a large number of accesses most likely made by some sort of program from a certain entity. Aside from the 17th and 19th, 18 out of 20 are the vulnerabilities published on JVN (Japan Vulnerability Notes). Vulnerabilities released on JVN includes those disclosed in accordance with the Information Security Early Warning Partnership (*14). Those vulnerabilities typically receive a lot of attention and are picked up by various news media and blogs, which probably made their access number up.
Rating Scale
Note 1) CVSSv2 Severity Rating Scale
- Level I (Low)
- CVSS Base Score = 0.0~3.9
- Level II (Medium)
- CVSS Base Score = 4.0~6.9
- Level III (High)
- CVSS Base Score = 7.0~10.0
Note 2) CVSSv3 Severity Rating Scale
- Low
- CVSS Base Score =0.1~3.9
- Medium
- CVSS Base Score =4.0~6.9
- High
- CVSS Base Score =7.0~8.9
- Critical
- CVSS Base Score =9.0~10.0
Table 3-1. Top 20 Most Accessed Vulnerability Countermeasure Information in JVN iPedia [Oct. – Dec. 2018]
No.1 Multiple vulnerabilities in FileZen JVNDB-2018-000104
- CVSSv2 Severity Rating Scale
-
- Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
- Critical
- CVSSv3 Base Score
-
10.0
- Date Public
-
2018/10/15
- Access Count
-
514,239
No.2 Multiple vulnerabilities in Denbun JVNDB-2018-000102
- CVSSv2 Severity Rating Scale
-
- Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2018/10/4
- Access Count
-
6,294
No.3 The installer of Baidu Browser may insecurely load Dynamic Link Libraries JVNDB-2018-000101
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2018/10/3
- Access Count
-
6,239
No.4 +Message App fails to verify SSL server certificates JVNDB-2018-000100
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.8
- Date Public
-
2018/9/27
- Access Count
-
5,843
No5. Multiple vulnerabilities in INplc JVNDB-2018-000092
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2018/9/7
- Access Count
-
5,643
No.6 Web Isolation vulnerable to cross-site scripting JVNDB-2018-000110
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
- Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/10/19
- Access Count
-
5,397
No.7 Music Center for PC improperly verifies software update files JVNDB-2018-000103
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
5.1
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2018/10/9
- Access Count
-
5,337
No.8 User-friendly SVN vulnerable to cross-site scripting JVNDB-2018-000106
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/10/9
- Access Count
-
5,284
No.9 OpenAM (Open Source Edition) vulnerable to session management JVNDB-2018-000107
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.0
- Date Public
-
2018/10/12
- Access Count
-
5,235
No.10 Metabase vulnerable to cross-site scripting JVNDB-2018-000105
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/10/11
- Access Count
-
5,104
No.11 Multiple vulnerabilities in i-FILTER JVNDB-2018-000129
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
- Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/12/7
- Access Count
-
5,100
No.12 BlueStacks App Player fails to restrict access permissions JVNDB-2018-000111
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
5.8
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.3
- Date Public
-
2018/10/24
- Access Count
-
5,045
No.13 Multiple vulnerabilities in YukiWiki JVNDB-2018-000109
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/10/19
- Access Count
-
4,969
No.14 Multiple vulnerabilities in OpenDolphin JVNDB-2018-000113
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.5
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
8.8
- Date Public
-
2018/10/26
- Access Count
-
4,956
No.15 Mail app for iOS vulnerable to denial-of-service (DoS) JVNDB-2018-000116
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.0
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2018/11/2
- Access Count
-
4,895
No.16 SecureCore Standard Edition vulnerable to authentication bypass JVNDB-2018-000112
- CVSSv2 Severity Rating Scale
-
- Level I (Low)
- CVSSv2 Base Score
-
2.1
- CVSSv3 Severity Rating Scale
-
- Low
- CVSSv3 Base Score
-
2.4
- Date Public
-
2018/10/24
- Access Count
-
4,758
No.17 Clickjacking Vulnerability in Hitachi Device Manager JVNDB-2018-008547
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2018/10/22
- Access Count
-
4,699
No.18 Cybozu Garoon vulnerable to directory traversal JVNDB-2018-000099
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.4
- Date Public
-
2018/9/10
- Access Count
-
4,617
No.19 Multiple Vulnerabilities in JP1/VERITAS JVNDB-2018-009328
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2018/11/15
- Access Count
-
4,586
No.20 IMultiple vulnerabilities in WordPress plugin "LearnPress" JVNDB-2018-000117
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.5
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.2
- Date Public
-
2018/11/9
- Access Count
-
4,576
Table 3-2 lists the top 5 most accessed vulnerability information among those reported by domestic software developers.
Table 3-2. Top 5 Most Accessed Vulnerabilities Reported by Domestic Developers [Oct. - Dec. 2018]
No.1 Clickjacking Vulnerability in Hitachi Device Manager JVNDB-2018-008547
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2018/10/22
- Access Count
-
4,699
No.2 Multiple Vulnerabilities in JP1/VERITAS JVNDB-2018-009328
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2018/11/15
- Access Count
-
4,586
No.3 DoS Vulnerability in JP1/ ServerConductor/ Deployment Manager and Hitachi Compute Systems Manager JVNDB-2018-002257
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2018/4/4
- Access Count
-
4,090
No.4 XXE Vulnerability in Hitachi Device Manager JVNDB-2018-001389
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.4
- Date Public
-
2018/2/14
- Access Count
-
4,076
No.5 Multiple Vulnerabilities in Hitachi Command Suite JVNDB-2018-001388
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.8
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/2/14
- Access Count
-
4,040
Footnotes
-
(*1)
-
(*2)
-
(*3)
-
(*4)
-
(*5)
-
(*6)
-
(*7)
-
(*8)
-
(*9)
-
(*10)
-
(*11)
-
(*12)
-
(*13)
-
(*14)
Past Quarterly Reports
Contact information
IT Security Center,
Information-technology Promotion Agency, Japan (ISEC/IPA)