Enhancing information security

Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2018 1st Quarter (Jan. - Mar.)]
Release Date:May 25, 2018
IT Security Center
1. 2018 1st Quarter: Vulnerability Countermeasure Information Database JVN iPedia Registration Status
The vulnerability countermeasure information database JVN iPedia (https://jvndb.jvn.jp/en/) is endeavoring to become a comprehensive vulnerability database where vulnerability information is aggregated for easy access for IT users. JVN iPedia collects and/or translates the vulnerability information published by 1) domestic software developers, 2) JVN (*1), a vulnerability information portal run by JPCERT/CC and IPA, and 3) NVD (*2), a vulnerability database run by NIST (*3). JVN iPedia has been making vulnerability information available to the public since April 25, 2007.
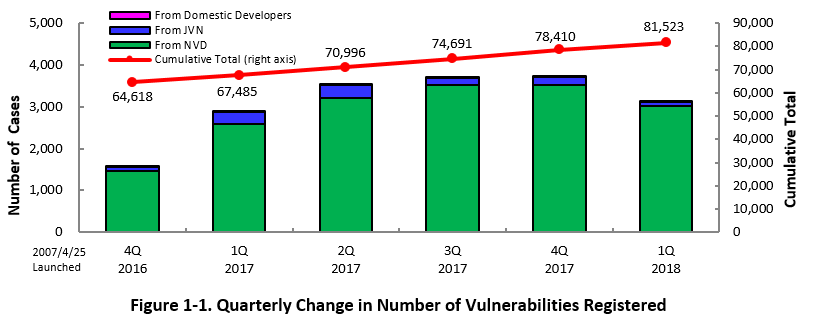
1-1. Vulnerabilities Registered in 2018/1Q
~ JVN iPedia now stores 81,523 vulnerabilities ~
The summary of the vulnerability information registered to the Japanese version of JVN iPedia during the 1st quarter of 2018 (January 1 to March 31, 2018) is shown in the table below. As of the end of March 2018, the total number of vulnerabilities stored in JVN iPedia is 81,523 (Table 1-1, Figure 1-1).
As for the English version, the total of 1,881 vulnerabilities are available as shown in the lower half of the table.
Table 1-1. Registered Vulnerabilities in 1st Quarter of 2018
|
|
Information Source
|
Registered Cases
|
Cumulative Cases
|
|---|---|---|---|
|
Japanese Version
|
Domestic Product Developers
|
2 cases
|
198 cases
|
|
JVN
|
89 cases
|
7,953 cases
|
|
|
NVD
|
3,022 cases
|
73,372 cases
|
|
|
Total
|
3,113 cases
|
81,523 cases
|
|
|
English Version
|
Domestic Product Developers
|
4 cases
|
198 cases
|
|
JVN
|
41 cases
|
1,683 cases
|
|
|
Total
|
45 cases
|
1,881 cases
|
2. Details on JVN iPedia Registered Data
2-1. Types of Vulnerabilities Reported
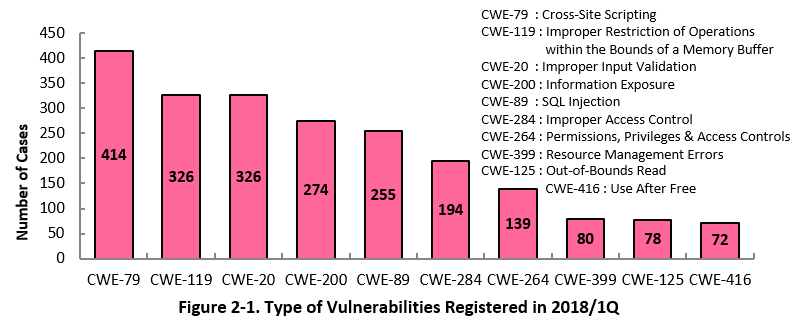
Figure 2-1 shows the number of vulnerabilities newly added to JVN iPedia during the 1st quarter of 2018, sorted by the CWE vulnerability types.
The type of the vulnerabilities reported most in the 1st quarter is CWE-79 (Cross-Site Scripting) with 414 cases, followed by CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer) with 326, CWE-20 (Improper Input Validation) with 326, CWE-200 (Information Exposure) with 274, CWE-89 (SQL Injection) with 255. CWE-79, the most reported vulnerability type this quarter, could allow attackers to redirect users to fake web pages or cause information exposure.
Software developers need to make sure to implement necessary security controls from the planning and design phase of software development to mitigate vulnerability. IPA provides tools and guidelines, such as "How to Secure Your Website" (*4), "Secure Programing Guide" (*5) and "AppGoat" (*6), a hands-on venerability learning tool, for website developers and operators to build secure websites.
2-2. Severity of Vulnerabilities Reported
Figure 2-2 shows the yearly change in the CVSSv2 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2018, 30.6 percent are "level III" (7.0 - 10.0), 57.9 percent are "level II" (4.0 – 6.9) and 11.5 percent are "level I" (0.0 – 3.9). This means 88.5 percent of all vulnerabilities registered are level II or higher, which are potentially critical enough to cause damage like information exposure or data modification.
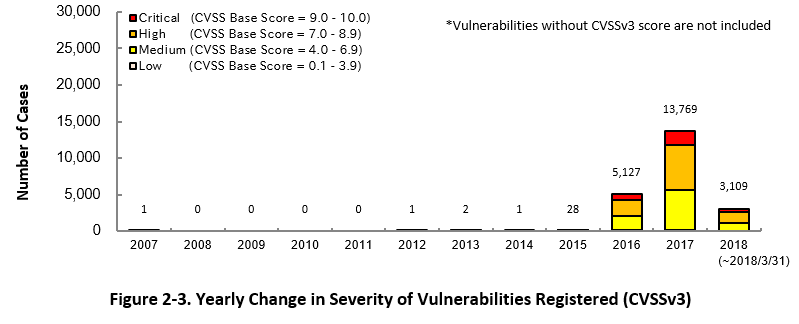
Figure 2-3 shows the yearly change in the CVSSv3 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2018, 17.0 percent are "Critical" (9.0 – 10.0), 45.1 percent are "High" (7.0 – 8.9), 36.6 percent are "Medium" (4.0 – 6.9) and 1.3 percent are "Low" (0.1 – 3.9).
To mitigate threats imposed by the known vulnerabilities, IT users should pay close attention to vulnerability information and update software they are using to a fixed version or apply a security patch as soon as possible when they become available.
When a serious vulnerability or attack is reported, IPA issues an emergency security alert. The alerts can be received as soon as they are issued through the service called "icat for JSON" (*7). IT users can also check vulnerabilities newly published on JVN iPeia via RSS feed as well.
2-3. Types of Software Reported with Vulnerability
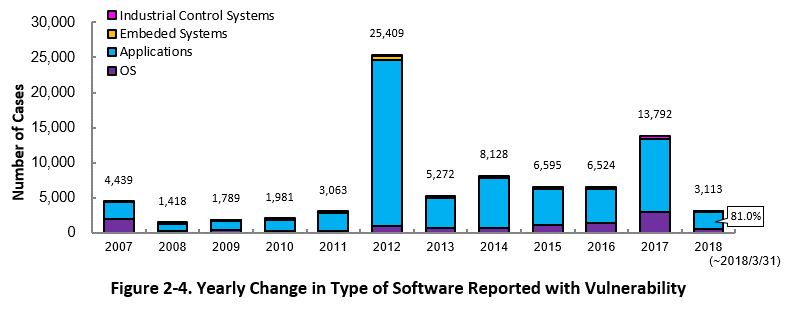
Figure 2-4 shows the yearly change in the type of software reported with vulnerability. Application vulnerabilities have been published most, accounting for 81.0 percent (2,520 out of 3,113) of the 2018 total.
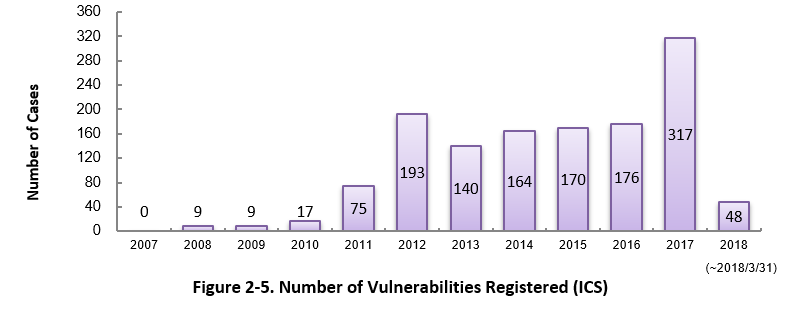
Since 2007, vulnerability in industrial control systems (ICS) used in critical infrastructure sectors has started to be added to JVN iPedia. As of March 2018, the total of 1,318 ICS vulnerabilities have been registered (Figure 2-5).
2-4. Products Reported with Vulnerability
Table 2-1 lists the top 20 software whose vulnerabilities were most registered to JVN iPedia during the 1st quarter (January to March) of 2018. A lot of Linux OS vulnerabilities were published, such as Debian GNU/Linux (ranked 1st with 117 vulnerabilities) and Linux Kernel (ranked 4th with 50 vulnerabilities).
Besides those in the top 20 list, JVN iPedia stores vulnerabilities about a variety of software used in office and at home. IPA hopes software developers and users will make good use of JVN iPedia to efficiently check vulnerability information about the software they are using and take necessary action in a timely manner (*8).
Table 2-1. Top 20 Software Products Vulnerabilities Were Most Registered [Jan. – Mar. 2018]
|
Rank
|
Category
|
Product Name (Vendor)
|
Number of
Vulnerabilities Registered |
|---|---|---|---|
|
1
|
OS
|
Debian GNU/Linux (Debian)
|
117
|
|
2
|
OS
|
Android (Google)
|
104
|
|
3
|
ERP Package
|
HPE Intelligent Management Center
(Hewlett Packard Enterprise) |
96
|
|
4
|
OS
|
Linux Kernel (Linux)
|
50
|
|
5
|
Browser
|
Microsoft Edge (Microsoft)
|
46
|
|
6
|
PDF Viewer
|
Foxit Reader (Foxit Software Inc)
|
43
|
|
6
|
Execution Environment
|
ChakraCore (Microsoft)
|
43
|
|
8
|
PDF Viewer
|
Adobe Reader (Adobe Systems)
|
39
|
|
8
|
PDF Viewer/Editor
|
Adobe Acrobat DC (Adobe Systems)
|
39
|
|
8
|
PDF Viewer
|
Adobe Acrobat Reader DC (Adobe Systems)
|
39
|
|
8
|
PDF Viewer/Editor
|
Adobe Acrobat (Adobe Systems)
|
39
|
|
12
|
Firmware
|
DP300 Firmware (Huawei)
|
36
|
|
13
|
OS
|
Microsoft Windows 10 (Microsoft)
|
35
|
|
14
|
OS
|
Microsoft Windows Server Version 1709 (Microsoft)
|
32
|
|
14
|
Firmware
|
TE30 Firmware (Huawei)
|
32
|
|
16
|
Firmware
|
RP200 Firmware (Huawei)
|
31
|
|
16
|
Image Processing
|
ImageMagick (ImageMagic)
|
31
|
|
18
|
Security Software
|
K7 Antivirus (K7 Computing)
|
29
|
|
18
|
OS
|
Microsoft Windows Server 2016 (Microsoft)
|
29
|
|
18
|
Network Analyzer
|
Wireshark (Wireshark)
|
29
|
3. Most Accessed Vulnerability Countermeasure Information
Table 3-1 lists the top 20 most accessed vulnerability information in JVN iPedia during the 1st quarter of 2018 (January – March).
The 1st ranked vulnerabilities, collectively named “Meltdown” and “Specter”, could affect a wide variety of products and drew lots of attention. The 4th tanked vulnerability in Oracle WebLogic Server was first published in October 2017, but is still ranked in the top 5 this quarter. Since attacks that exploited this vulnerability were observed in late December 2017, IPA issued an emergency security alert in January 2018 (*9), making it a high-profile vulnerability in 2018 as well.
Table 3-1. Top 20 Most Accessed Vulnerability Countermeasure Information in JVN iPedia [Jan. – Mar. 2018]
No.1 Side channel attacks to CPU JVNDB-2018-001001
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.4
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.7
- Date Public
-
2018/1/4
- Access Count
-
18,016
No.2 Lhaplus vulnerable to improper verification when expanding ZIP64 archives JVNDB-2018-000001
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Low
- CVSSv3 Base Score
-
3.3
- Date Public
-
2018/1/11
- Access Count
-
8,171
No.3 Spring Security and Spring Framework vulnerable to authentication bypass JVNDB-2018-000008
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.3
- Date Public
-
2018/2/2
- Access Count
-
7,070
No.4 Vulnerability in WLS Security in Oracle WebLogic Server in Oracle Fusion Middleware JVNDB-2017-008734
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2017/10/26
- Access Count
-
6,137
No5. Insecure DLL Loading issue in multiple Trend Micro products JVNDB-2018-000013
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2018/2/15
- Access Count
-
6,111
No.6 Updates released for multiple vulnerabilities in Apache Tomcat JVNDB-2018-001570
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2018/2/26
- Access Count
-
5,286
No.7 GroupSession vulnerable to open redirect JVNDB-2018-000003
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.7
- Date Public
-
2018/1/19
- Access Count
-
4,735
No.7 Nootka App for Android vulnerable to OS command injection JVNDB-2018-000002
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.1
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2018/1/19
- Access Count
-
4,735
No.9 XXE Vulnerability in Hitachi Device Manager JVNDB-2018-001389
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.4
- Date Public
-
2018/2/14
- Access Count
-
4,676
No.10 The installer of Anshin net security for Windows may insecurely load Dynamic Link Libraries JVNDB-2018-000009
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2018/2/6
- Access Count
-
4,475
No.11 Multiple Vulnerabilities in Hitachi Command Suite JVNDB-2018-001388
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.8
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2018/2/14
- Access Count
-
4,444
No.12 Qt for Android environment variables alteration JVNDB-2017-000247
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.1
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.3
- Date Public
-
2017/12/11
- Access Count
-
4,437
No.13 Multiple vulnerabilities in Wireless mobile storage "Digizo ShAirDisk" PTW-WMS1 JVNDB-2017-000241
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2017/11/30
- Access Count
-
4,415
No.14 Application and self-extracting archive containing the application of "FLET'S v4/v6 address selection tool" may insecurely load Dynamic Link Libraries JVNDB-2018-000014
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2018/2/13
- Access Count
-
4,398
No.15 Robotic appliance COCOROBO vulnerable to session management JVNDB-2017-000238
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.6
- Date Public
-
2017/11/16
- Access Count
-
4,384
No.16 Multiple vulnerabilities in WXR-1900DHP2 JVNDB-2018-000017
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
8.3
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
8.8
- Date Public
-
2018/2/26
- Access Count
-
4,372
No.17 Multiple vulnerabilities in multiple Buffalo broadband routers JVNDB-2017-000244
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2017/12/1
- Access Count
-
4,336
No.18 The installer of "FLET'S VIRUS CLEAR Easy Setup & Application Tool" and "FLET'S VIRUS CLEAR v6 Easy Setup & Application Tool" may insecurely load Dynamic Link Libraries JVNDB-2018-000004
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2018/1/22
- Access Count
-
4,322
No.19 The installer of The Public Certification Service for Individuals "The JPKI user's software" may insecurely load Dynamic Link Libraries JVNDB-2017-000245
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.8
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.8
- Date Public
-
2017/12/6
- Access Count
-
4,297
No.20 QND Advance/Standard vulnerable to directory traversal JVNDB-2017-009884
- CVSSv2 Severity Rating Scale
-
9.4
- CVSSv2 Base Score
-
9.4
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.1
- Date Public
-
2017/11/28
- Access Count
-
4,277
Table 3-2 lists the top 5 most accessed vulnerability information among those reported by domestic product developers.
Table 3-2. Top 5 Most Accessed Vulnerabilities Reported by Domestic Developers [Jan. - Mar. 2018]
No.1 Cross-site Scripting Vulnerability in Fujitsu NetCOBOL Cross-site Scripting Vulnerability in Fujitsu NetCOBOL
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.8
- Date Public
-
2017/12/8
- Access Count
-
3,987
No.2 Cross-site Scripting Vulnerability in Fujitsu Interstage List Works JVNDB-2017-004687
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.1
- Date Public
-
2017/7/5
- Access Count
-
3,785
No.3 Cross-site Scripting Vulnerability in JP1/Service Support and JP1/Integrated Management - Service Support JVNDB-2017-010275
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.1
- Date Public
-
2017/12/11
- Access Count
-
3,402
No.4 Cross-site Scripting Vulnerability in JP1/Operations Analytics Cross-site Scripting Vulnerability in JP1/Operations Analytics
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.1
- Date Public
-
2017/12/1
- Access Count
-
3,294
No.5 XXE Vulnerability in Hitachi Command Suite JVNDB-2017-008411
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
8.1
- Date Public
-
2017/10/18
- Access Count
-
3,247
Footnotes
-
(*1)
-
(*2)
-
(*3)
-
(*4)
-
(*5)
-
(*6)
-
(*7)
-
(*8)
-
(*9)
Past Quarterly Reports
Contact information
IT Security Center, Information-technology Promotion Agency, Japan (ISEC/IPA)