Enhancing information security

Vulnerabilities:CWE (Common Weakness Enumeration) Overview
Last Updated:Apr 5, 2022
IT Security Center
Information-technology Promotion Agency, Japan
A list of software weakness types to provide a common language for identifying the type of vulnerability
>> JAPANESE
CWE (Common Weakness Enumeration)(*1) aims to provide a common base to identify the type of software weakness (vulnerability).
Leading the effort with support from the U.S. government, MITRE(*2) had been working on a specification since 1999 and published the first draft in March 2006. More than 40 vendors and research entities have joined hands to improve and expand the specification since then and the version 1.0 of CWE was published on September 9, 2008.
CWE gives a hierarchically structured list of weakness types to help identifying software vulnerabilities that come in a wide variety, such as SQL injection, cross-site scripting and buffer overflow. The use of CWE will enable software developers and security experts to:
- Have a common language to discuss software vulnerability in architecture, design and code.
- Use as a standard measuring rule for security tools, such as a vulnerability scanning tool, to enhance software security.
- Use as a common foundation to understand, mitigate and prevent vulnerability.
CWE has been adopted by NIST(*3) for NVD(*4), OWASP(*5) for Top Ten Project(*6) and other security vendors.
This overview is based on CWE Version 1.5, released by MITRE. For more information, please refer to MITRE CWE List.
1.CWE Structure
CWE organizes a wide variety of weakness types in a hierarchical structure and gives a unique identifier (CWE-ID) to each type. The weakness types at higher levels in the structure gives a more abstract and broader concept, while those at deeper level gives a more concrete concept or represent an actual CWE entity.
There are four structural classifications in CWE: View, Category, Weakness and Compound Element. Currently, 22 weakness types are classified as View, 105 as Category, 638 as Weakness and 12 as Compound Element. In total, 777 CWE entries are defined and organized in the list.
(1)View
Each View entry represents a perspective with which one may use CWE and organizes weakness types from the perspective. For example, NIST has handpicked 19 weakness types from CWE based on the vulnerabilities published on NVD and lists them on its Web site (CWE Cross Section Mapped into by NVD). The View that consists of those 19 weakness types is being given the CWE-ID of CWE-635, Weaknesses Used by NVD.
Likewise, CWE-699 is the View organized from the perspective of developers, CWE-1000 from that of researchers, CWE-658 from that of C and CWE-660 from that of Java.
(2)Category
Each Category entry, given a “grouping” capability, represents a collection of weakness types that share a common characteristic.
For instance, CWE-310 is a group of weakness types with cryptographic issues and CWE-355 with user interface issues.
(3)Weakness
Each Weakness entry represents an actual CWE entity and is subsequently classified using three attributes: Class, Base and Variant.
The Class attribute suggests the most abstract type of weakness of the three. CWE-362, Race Condition, is an example of this type.
The Base attribute suggests a more specific type of weakness that is independent of specific technology or resource. CWE-567, Unsynchronized Access To Shared Data, is an example of this type.
The Variant attribute suggests a specific type of weakness that is dependent of particular resource, technology or context. CWE-488, Data Leak Between Sessions, is an example of this type.
(4)Compound Element
Each Compound Element entry represents an aggregation of related weakness types with a composite nature and is subsequently classified using two attributes: Composite and Chain.
The Composite attribute suggests a case where a weakness emerges in combination of another weakness. CWE-352, Cross-Site Request Forgery, is an example of this type.
The Chain attribute suggests a case where a weakness results in another weakness. CWE-680, Integer Overflow to Buffer Overflow, is an example of this type.
2.Elements of CWE
The CWE List is organized by CWE-ID and each CWE entry is provided with various information. To name a few, the CWE elements include Description, Likelihood of Exploit, Common Consequences, Potential Mitigations, Demonstrative Examples and Observed Example.
Users could use the CWE List as reference to identity, mitigate and prevent vulnerabilities.
3.JVN iPedia declared CWE-Compatible
JVN iPedia began to support CWE as a trial on September 10, 2008(*7). IPA had worked on a few remaining requirements to make a CWE compatibility declaration and declared it CWE-Compatible on October 3, 2008.
The official list of organizations participating in the CWE Compatibility and Effectiveness Program is available on Mitre’s CWE web site.
http://cwe.mitre.org/compatible/organizations.html
MyJVN began to support CWE on October 23, 2008(*8).
The four mandatory requirements – “CWE Searchability”, “CWE Output”, “CWE Documentation” and “Mapping Accuracy” – for phase 1 are fulfilled by the functions illustrated in Table 1.
| CWE Searchability |
|
|---|---|
| CWE Output |
|
| CWE Output |
|
| CWE Documentation |
|
| Mapping Accuracy |
|
Figure 1 shows a hierarchical structure of weakness types to be used by JVN iPedia. It is based on Development View with Abstractions Highlighted, which is a graph that depicts the hierarchical structure of a View organized from the perspective of developers.
The yellow-colored ones are to be used by JVN iPedia. For the overall hierarchical structure of the CWE List, please refer to PDFs with Graphical Depictions of CWE (1.5).
IPA will revise the weakness types, analyzing the vulnerabilities published on JVN iPedia, and consider expanding them to include the deeper level of weakness types to support frequently-reported vulnerabilities.
-
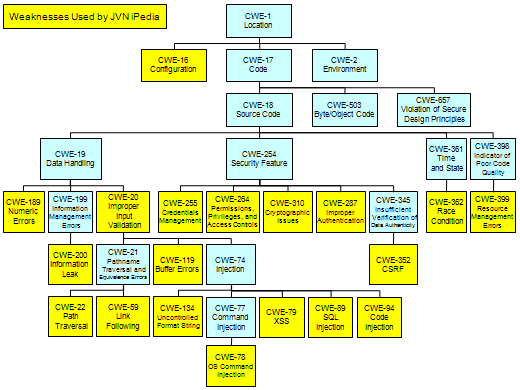
Figure1. Hierarchical Structure of Weakness Types Used by JVN iPedia
4.Weakness Types Used by JVN iPedia
Table 2 is a list of weakness types to be used by JVN iPedia.
From #20 to #23 are weakness types not classifiable by CWE-635, #20 corresponds to a CWE other than CWE-635, #21 is not classifiable by CWE, #22 needs more information to determine and #23 is about design problem.
| #1 Configuration |
|
|---|---|
| #2 Improper Input Validation |
|
| #3 Path Traversal |
|
| #4 Link Following |
|
| #5 OS Command Injection |
|
| #6 Cross-site scripting (XSS) |
|
| #7 SQL Injection |
|
| #8 Code Injection |
|
| #9 Improper Restriction of Operations within the Bounds of a Memory Buffer (Buffer Errors) |
|
| #10 Use of Externally-Controlled Format String |
|
| #11 Numeric Errors |
|
| #12 Information Exposure (Information Disclosure/Information Leak) |
|
| #13 Credentials Management |
|
| #14 Permissions, Privileges, and Access Controls |
|
| #15 Improper Authentication |
|
| #16 Cryptographic Issues |
|
| #17 Cross-Site Request Forgery (CSRF) |
|
| #18 Race Condition |
|
| #19 Resource Management Errors |
|
| #20 No Mapping |
|
| #21 No Mapping |
|
| #22 No Mapping |
|
| #23 No Mapping |
|
Footnotes
(*1)CWE: Common Weakness Enumeration.
http://cwe.mitre.org/index.html
(*2)MITRE Corporation: A not-for-profit organization that provides information technology support and R&D development to the U.S. government.
http://www.mitre.org/
(*3)NIST: National Institute of Standards and Technology. A federal agency that develops and promotes measurement, standards and technology.
http://www.nist.gov/
(*4)NVD: National Vulnerability Database. A vulnerability database run by NIST.
http://nvd.nist.gov/
(*5)OWASP: Open Web Application Security Project. An open, not-for-profit community dedicated to enhancing software security by developing open source software to secure Web applications and Web sites and promoting software security.
http://www.owasp.org/
(*6)OWASP Top Ten Project: A security awareness promotion with which OWASP picks top ten of the most critical Web application security vulnerabilities. http://www.owasp.org/index.php/OWASP_TOP_TEN_PROJECT
(*7)JVN iPedia Upgraded to New Version. http://www.ipa.go.jp/security/english/vuln/200809_JVN_iPedia_en.html
(*8)Filtered Vulnerability Countermeasure Information Tool “MyJVN” Now Available. http://www.ipa.go.jp/security/english/vuln/200810_MyJVN_en.html
Filtered Vulnerability Countermeasure Information Tool “MyJVN” English Version Released. http://www.ipa.go.jp/security/english/vuln/200901_myjvn_english_en.html
Reference
- CVE (Common Vulnerabilities and Exposures) Overview
- CPE (Common Platform Enumeration) Overview
- OVAL (Open Vulnerability and Assessment Language) Overview
Contact information
IT Security Center,
Information-technology Promotion Agency, Japan (ISEC/IPA)
-
E-mail
Change log
-
Mar 5, 2022
Updated description in Table 2.
-
Aug 5, 2009
Adopt CWE 1.5
-
Jun 3, 2009
Adopt CWE 1.4
-
Sep 10, 2008
Release
