Enhancing information security

Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2021 4th Quarter (Oct. - Dec.)]
Release Date:Feb 16, 2022
IT Security Center
1. 2021 4th Quarter: Vulnerability Countermeasure Information Database JVN iPedia Registration Status
The vulnerability countermeasure information database JVN iPedia (https://jvndb.jvn.jp/en/) is endeavoring to become a comprehensive vulnerability database where vulnerability information is aggregated for easy access for IT users. JVN iPedia collects and/or translates the vulnerability information published by 1) domestic software developers, 2) JVN (*1), a vulnerability information portal run by JPCERT/CC and IPA, and 3) NVD (*2), a vulnerability database run by NIST (*3). JVN iPedia has been making vulnerability information available to the public since April 25, 2007.
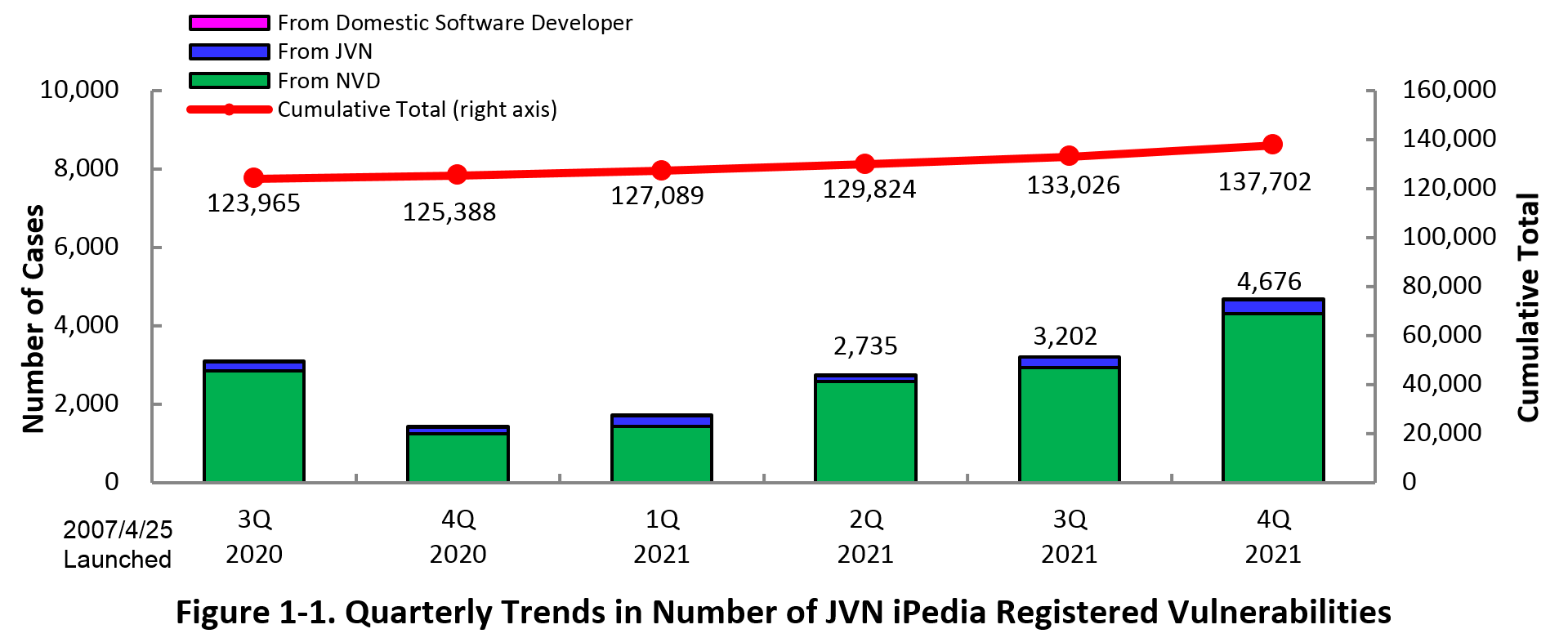
1-1. Vulnerabilities Registered in 2021/4Q
~ JVN iPedia now stores 137,702 vulnerabilities ~
The summary of the vulnerability information registered to the Japanese version of JVN iPedia during the 4th quarter of 2021 (October 1 to December 31, 2021) is shown in the table below. As of the end of December 2021, the total number of vulnerabilities stored in JVN iPedia is 137,702 (Table 1-1, Figure 1-1).
As for the JVN iPedia English version, the total number of vulnerabilities stored is 2,375 as shown in the lower half of the Table 1-1.
Table 1-1. Vulnerabilities Registered to JVN iPedia during 4th Quarter of 2021
|
|
Information Source
|
Registered Cases
|
Cumulative Cases
|
|---|---|---|---|
|
Japanese Version
|
Domestic Product Developers
|
5 cases
|
261 cases
|
|
JVN
|
358 cases
|
10,814 cases
|
|
|
NVD
|
4,313 cases
|
126,627 cases
|
|
|
Total
|
4,676 cases
|
137,702 cases
|
|
|
English Version
|
Domestic Product Developers
|
5 cases
|
256 cases
|
|
JVN
|
33 cases
|
2,119 cases
|
|
|
Total
|
38 cases
|
2,375 cases
|
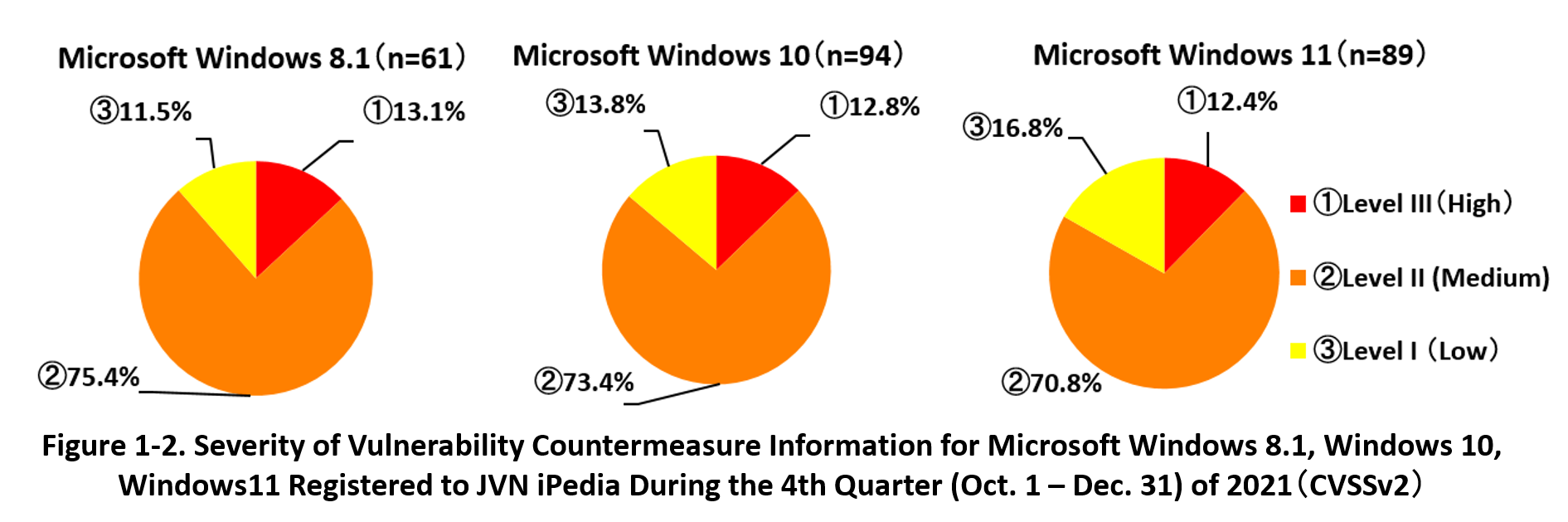
1-2. 【Observation 1】Vulnerabilities in Microsoft Windows Products
~Vulnerabilities classified as the highest severity 'High' discovered in a new product 'Microsoft Windows 11' released in October, 2021. Continue to take vulnerability countermeasures~
Microsoft Windows 11 was released on October 5, 2021. This product attracted attention for the successor version of Windows 10, and the number of users has been gradually increasing as it can be upgraded free of charge. Microsoft claims that Windows 11 added a variety of new features and enhanced security such as adopting the Zero Trust concept.(*4)
On the other hand, a number of vulnerabilities have already been discovered and disclosed in Windows 11. 89 cases of vulnerability countermeasure information have registered to JVN iPedia since its release until the end of December 2021. Vulnerabilities classified as 'High' are included among them.
Figure 1-2 shows the percentage of severity of vulnerability countermeasure information registered to JVN iPedia for Windows 8.1, Windows 10, and Windows 11 which are currently supported by Microsoft. As for Windows 11, 12.4% of vulnerabilities are classified as the highest severity 'High' (CVSS base score=7.0-10.0), 70.8% are the next highest severity 'Medium' (CVSS base score =4.0-6.9), and 16.9% are 'Low' (CVSS base score= 0.1-3.9). The result indicates that the vulnerabilities classified as 'High' and 'Medium' are dominated more than 80%. There was not significant difference in the percentage of severity of vulnerability compared to Windows 8.1 and Windows 10. Therefore, it is expected that vulnerability countermeasure information for Windows 11 will continue to be discovered and disclosed in 2022 and beyond in the same trend as the previous Windows OS.
In order to resolve these vulnerabilities and use Windows 11 securely, users are recommended to immediately apply security patches released by Microsoft, as with conventional Microsoft products. IPA publishes alert information as important security information when Microsoft releases its monthly security patches. IPA also provides a service called "icat for JSON" (IPA Cyber security Alert Service for JavaScript Object Notation) (*5) that promptly disseminates the information to the employees of organizations and users of published services, so please take advantage of this service as well.
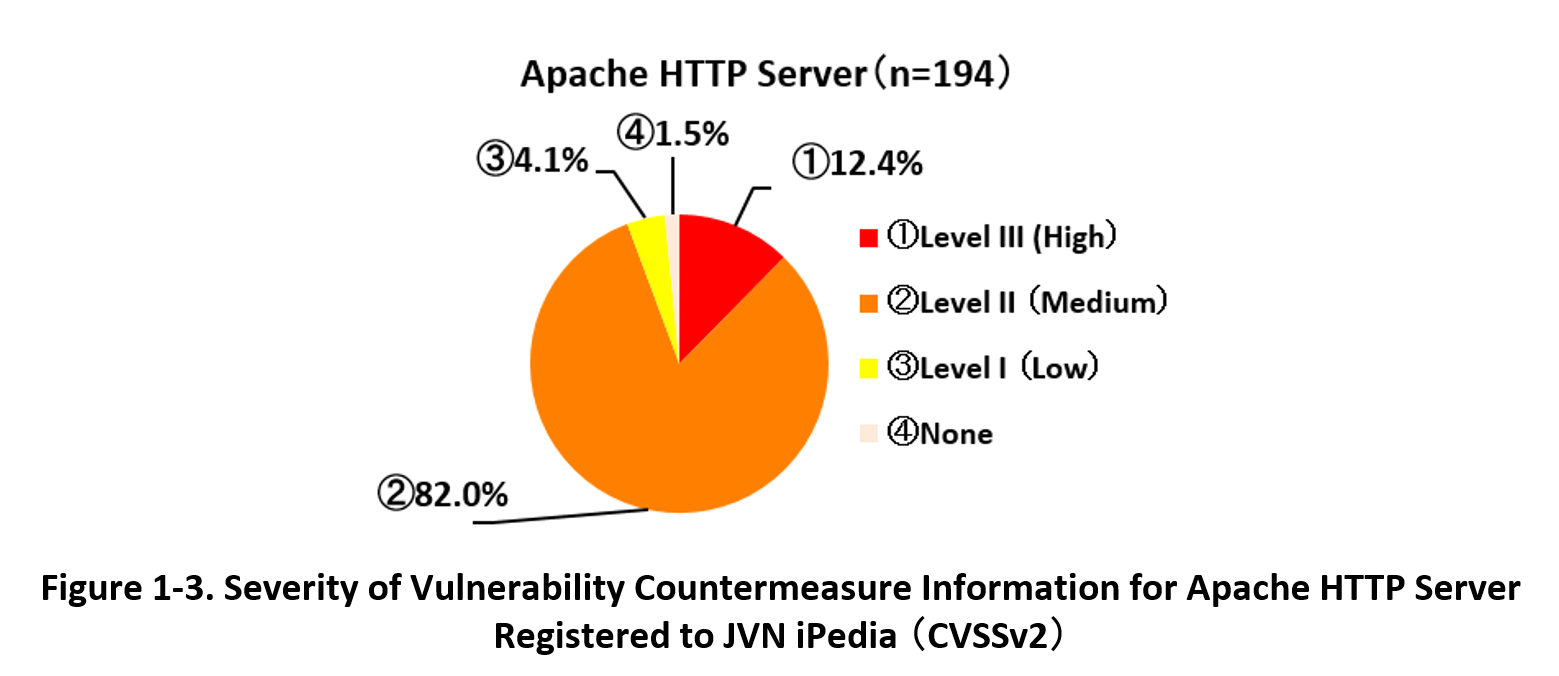
1-3. 【Observation 2】Vulnerabilities in Apache HTTP Server
~Attacks that exploit a path traversal vulnerability (CVE-2021-41773) have been confirmed in Japan~
In October 2021, the Apache Software Foundation released vulnerability information of Apache HTTP Server (CVE-2021-41773), and several public organizations, including IPA, issued an alert that the vulnerability had been confirmed to be exploited.(*6)(*7)
The vulnerability is a path traversal vulnerability that may allow access to files outside the document root, and if exploited, may allow remote attackers to manipulate files illegally. CVSS Base Score, which indicates the severity of the vulnerability, was 4.3 (*8) and classified as the second highest 'Medium' (CVSS Base Score=4.0-6.9) , but it was not a particularly high value. However, as several exploit codes were disclosed and attacks were confirmed in Japan, organizations using the affected versions of the vulnerability were required to take countermeasures.
In addition, within a few days, another path traversal vulnerability CVE-2021-42013 was revealed to exist in the version of Apache HTTP Server that was released as a fix for CVE-2021-41773. This vulnerability was classified as 'High' (CVSS Base Score=7.0-10.0) with CVSSv2 Base Score of 7.5. (*9) As with CVE-2021-41773, exploit codes for this vulnerability were confirmed, and since it was discovered immediately after the release of modified version of CVE-2021-41773, it has been posted on the Internet (*10) and attracted wide attention.
Apache HTTP Server is a web server program provided by the Apache Software Foundation as open source software. A total of 194 vulnerability countermeasure information for this product has been registered in JVN iPedia until the end of 2021. Figure 1-3 shows the percentage of the severity of vulnerability countermeasure information for Apache HTTP Server registered to JVN iPedia. 12.4% of vulnerabilities are classified as the highest severity 'High' (CVSS base score=7.0-10.0), 82.0% are the next highest severity 'Medium' (CVSS base score =4.0-6.9), and 4.1% are 'Low' (CVSS base score= 0.1-3.9). The result indicates that the vulnerabilities classified as 'High' and 'Medium' dominates, indicating that the vulnerabilities could have a significant impact if exploited.
Widely used Software like Apache HTTP Server attracts the attention of attackers when vulnerability information is disclosed and may be exploited in attacks. Users are recommended to collect vulnerability information and immediately apply security patches when they are released.
2. Details on JVN iPedia Registered Data
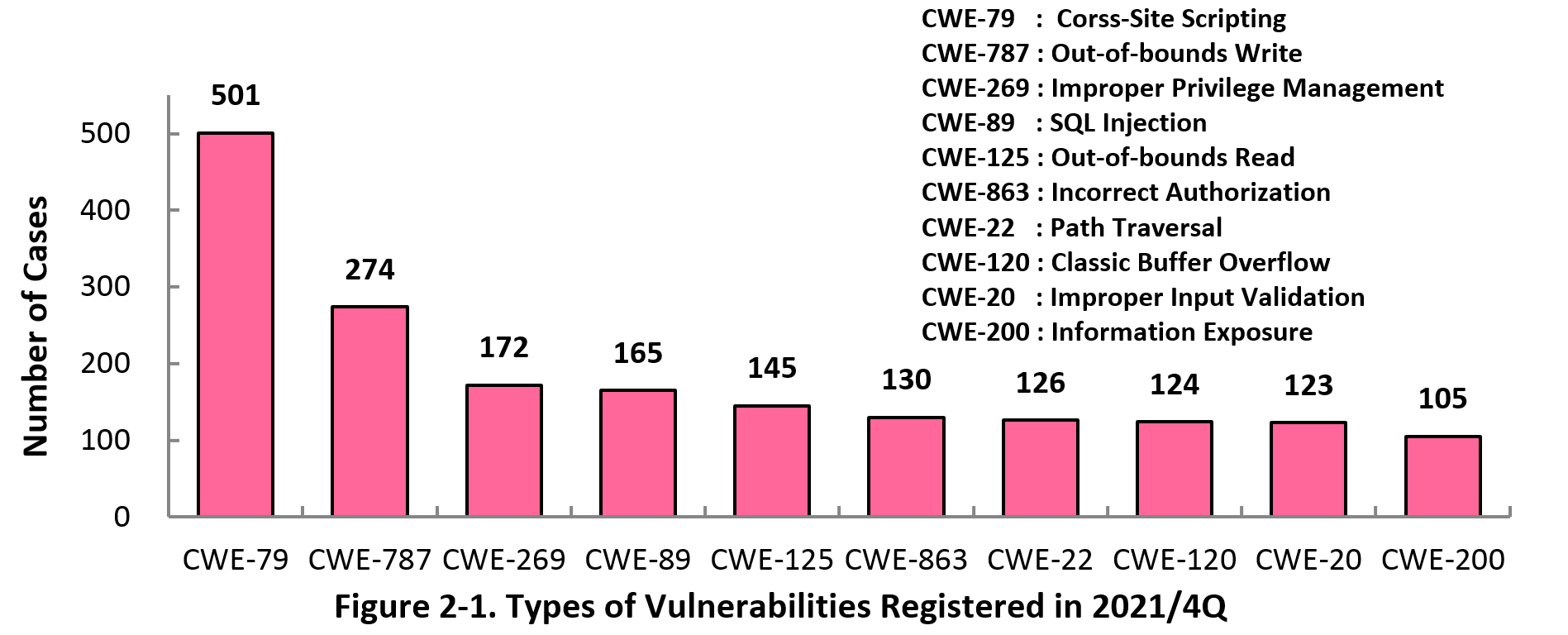
2-1. Types of Vulnerabilities Reported
Figure 2-1 shows the number of vulnerabilities newly added to JVN iPedia during the 4th quarter of 2021, sorted by the CWE vulnerability types.
The type of the vulnerabilities reported most in the 4th quarter is CWE-79 (Cross-Site Scripting) with 501 cases, followed by CWE-787 (Out-of-bounds Write) with 274, CWE-269 (Improper Privilege Management) with 172, CWE-89 (SQL Injection) with 165, CWE-125 (Out-of-bounds Read) with 145. CWE-79 (Cross-Site Scripting), the most reported vulnerability type in this quarter, could allow attackers to display false webpages and/or steal information.
Software developers need to make sure to mitigate vulnerability from the planning and design phase of software development. IPA provides tools and guidelines, such as "Vulnerability Countermeasure Guide for Software Developers"" (*11), "How to Secure Your Website" (*12), "Secure Programming Guide" (*13) and "AppGoat" (*14), a hands-on venerability learning tool, for website developers and operators to build secure websites.
2-2. Severity of Vulnerabilities Reported
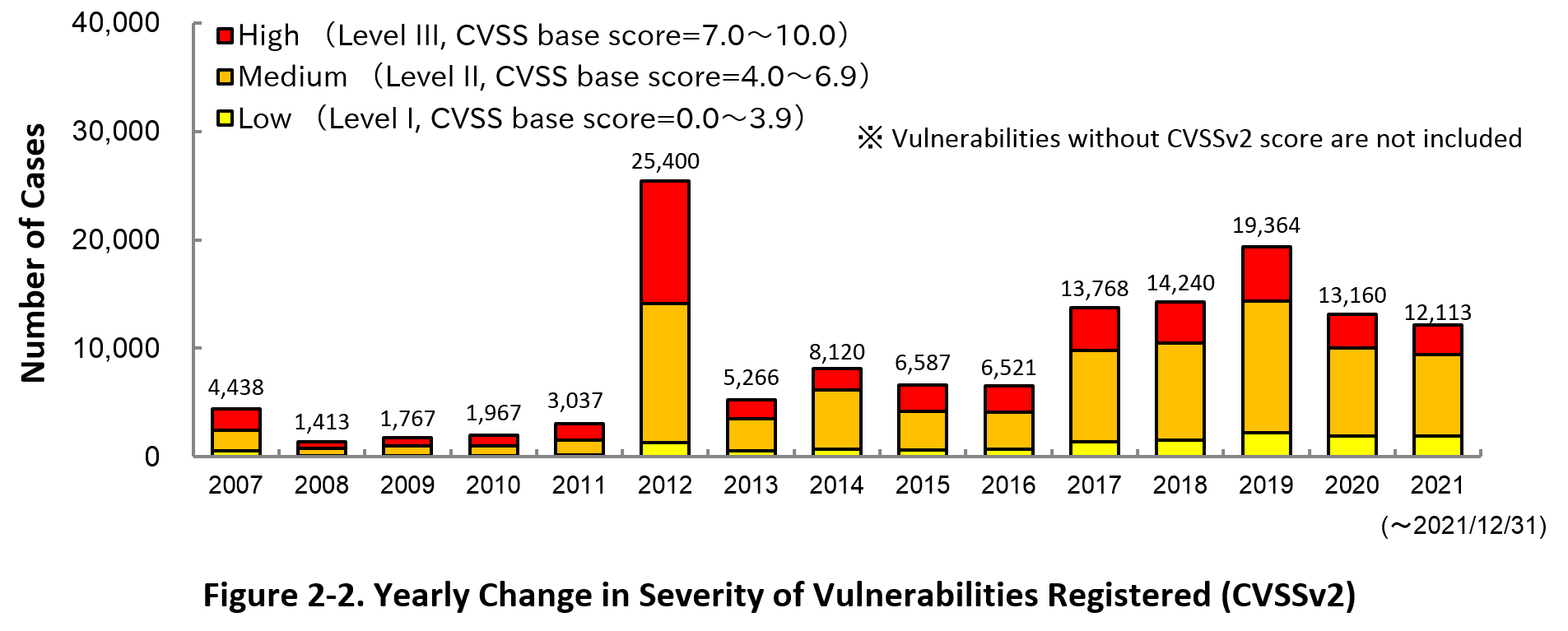
Figure 2-2 shows the yearly change in the CVSSv2 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2021, 22.2 percent are “Level III” (7.0 - 10.0), 62.2 percent are “Level II” (4.0 – 6.9) and 15.6 percent are “Level I” (0.0 – 3.9). This means 84.4 percent of all vulnerabilities registered are Level II or higher, which are potentially critical enough to cause damage like information exposure or data falsification.
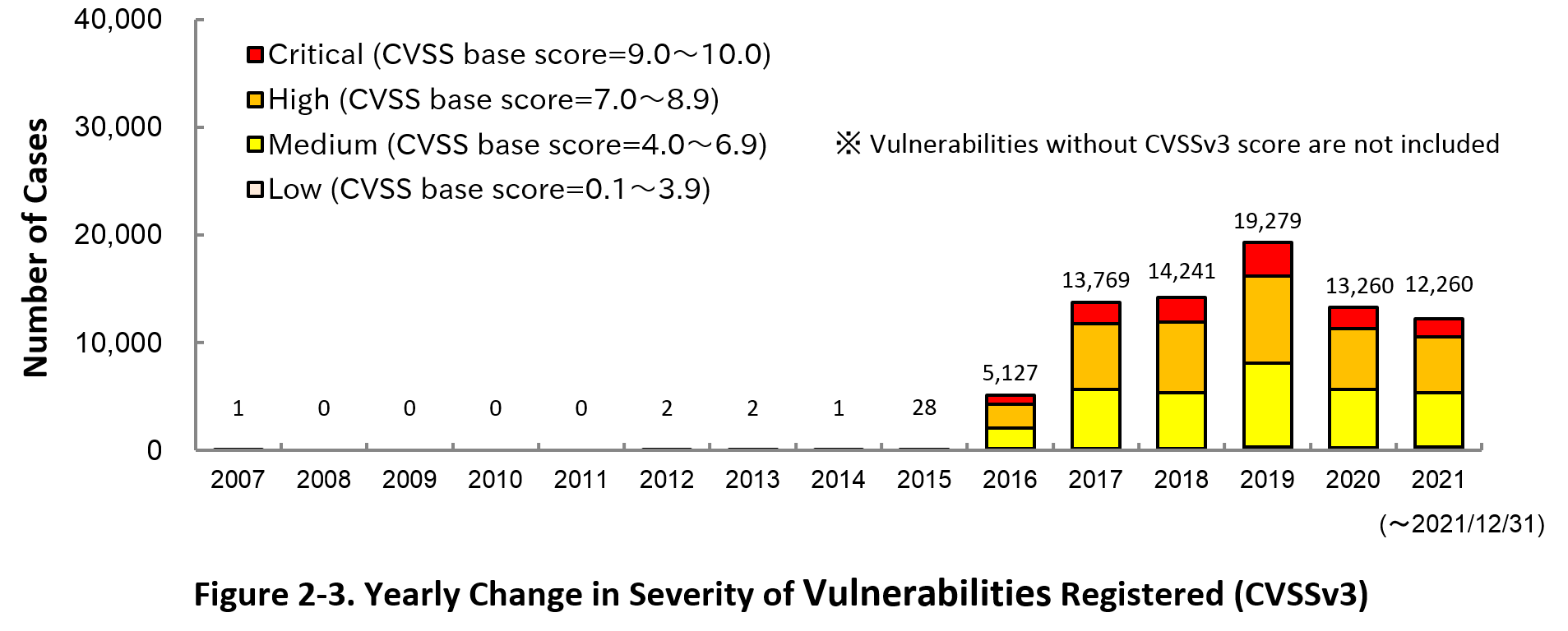
Figure 2-3 shows the yearly change in the CVSSv3 rating scale based severity of vulnerabilities registered to JVN iPedia.
As for the vulnerabilities added to JVN iPedia in 2021, 14.1 percent are “Critical” (9.0 – 10.0), 42.3 percent are “High” (7.0 – 8.9), 41.0 percent are “Medium” (4.0 – 6.9) and 2.5 percent are “Low” (0.1 – 3.9).
To avoid threats posed by the known vulnerabilities, both product developers and IT users should pay close attention to vulnerability disclosure and update software they use to a fixed version or apply a security patch as soon as possible when they become available. IT users can check vulnerabilities newly published on JVN iPedia in RSS and XML format (*15) as well.
2-3. Types of Software Reported with Vulnerability
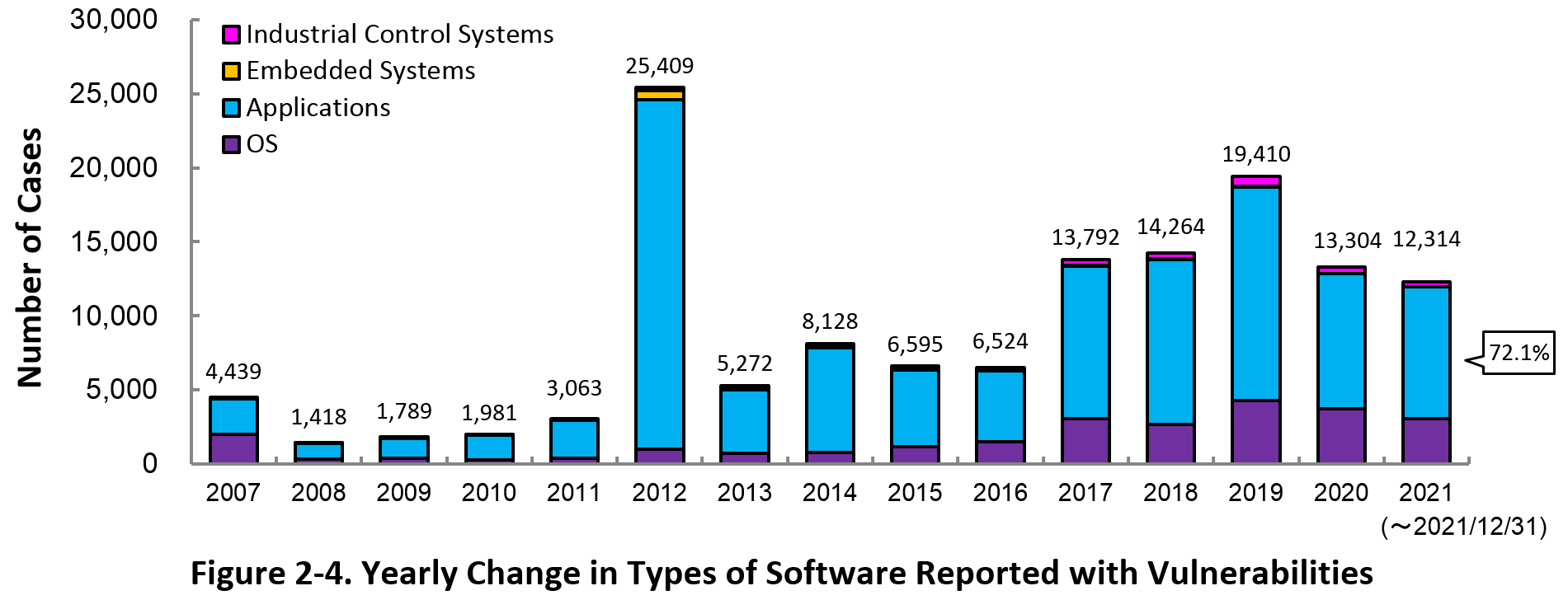
Figure 2-4 shows the yearly change in the type of software reported with vulnerability. Application vulnerabilities have been published most, accounting for 72.1 percent (8,884 out of 12,314) of the 2021 total.
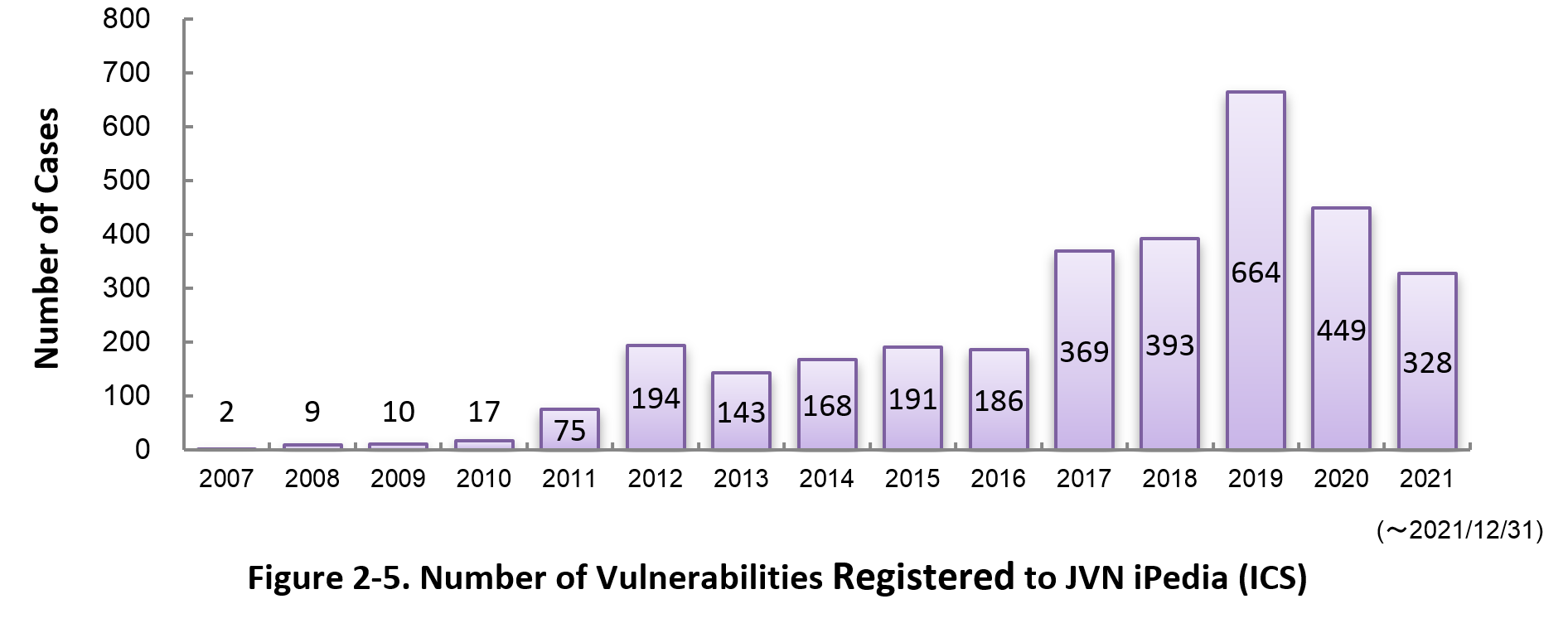
Figure 2-5 shows the yearly change in the number of JVN iPedia-stored vulnerabilities in industrial control systems (ICS) used in critical infrastructure sectors. As of December 2021, the total of 3,198 ICS vulnerabilities have been registered.
2-4. Products Reported with Vulnerability
Table 2-1 lists the top 20 software whose vulnerabilities were most registered to JVN iPedia during the 4th quarter (October to December) of 2021.
In this quarter, the most registered products were Qualcomm products. Qualcomm products were also the most registered products during the quarter in the 1st, 2nd and 4th quarter of 2021.
Besides those in the top 20 list, JVN iPedia stores and offers vulnerability information about a variety of software. IPA hopes software developers and users will make good use of JVN iPedia to efficiently check vulnerability information and take necessary action in a timely manner (*16).
Table 2-1. Top 20 most registered software products vulnerability countermeasure information in JVN iPedia [Oct. – Dec. 2021]
|
Rank
|
Category
|
Product Name (Vendor)
|
Number of
Vulnerabilities Registered |
|---|---|---|---|
|
1
|
Firmware
|
Qualcomm component (Qualcomm)
|
979
|
|
2
|
OS
|
Fedora (Fedora Project)
|
292
|
|
3
|
OS
|
Debian GNU/Linux (Debian)
|
186
|
|
4
|
OS
|
Android (Google)
|
155
|
|
5
|
Browser
|
Google Chrome (Google)
|
110
|
|
6
|
OS
|
Microsoft Windows Server (Microsoft)
|
102
|
|
7
|
OS
|
Microsoft Windows Server 2022 (Microsoft)
|
98
|
|
8
|
OS
|
Microsoft Windows 10 (Microsoft)
|
96
|
|
9
|
OS
|
Microsoft Windows Server 2019 (Microsoft)
|
95
|
|
10
|
OS
|
Microsoft Windows 11 (Microsoft)
|
89
|
|
11
|
OS
|
Microsoft Windows Server 2016 (Microsoft)
|
81
|
|
12
|
Others
|
OnCommand Insight (NetApp)
|
68
|
|
12
|
OS
|
Microsoft Windows Server 2012 (Microsoft)
|
68
|
|
14
|
OS
|
Microsoft Windows 8.1 (Microsoft)
|
63
|
|
15
|
OS
|
Microsoft Windows RT 8.1 (Microsoft)
|
62
|
|
16
|
OS
|
Linux Kernel (Kernel.org)
|
56
|
|
17
|
Others
|
SnapCenter (NetApp)
|
55
|
|
17
|
OS
|
Red Hat Enterprise Linux (Red Hat)
|
55
|
|
17
|
OS
|
Microsoft Windows Server 2008 (Microsoft)
|
55
|
|
20
|
OS
|
Microsoft Windows 7 (Microsoft)
|
51
|
3. Most Accessed Vulnerability Countermeasure Information
Table 3-1 lists the top 20 most accessed vulnerability countermeasure information in JVN iPedia during the 4th quarter of 2021 (October to December).
The first, second, and third rank vulnerabilities in this quarter were confirmed exploited attacks in Japan respectively and became a hot topic. Especially, vulnerability in Apache Log4j ranked in the second received more than 10,000 accesses as of the end of December, although it was disclosed on December 14, 2021.
Rating Scale
Note 1) CVSSv2 Severity Rating Scale
- Level I (Low)
- CVSS Base Score = 0.0~3.9
- Level II (Medium)
- CVSS Base Score = 4.0~6.9
- Level III (High)
- CVSS Base Score = 7.0~10.0
Note 2) CVSSv3 Severity Rating Scale
- Low
- CVSS Base Score =0.1~3.9
- Medium
- CVSS Base Score =4.0~6.9
- High
- CVSS Base Score =7.0~8.9
- Critical
- CVSS Base Score =9.0~10.0
Table 3-1. Top 20 Most Accessed Vulnerability Countermeasure Information in JVN iPedia [Oct. – Dec. 2021]
No.1 Movable Type XMLRPC API vulnerable to OS command injection JVNDB-2021-000093
- CVSSv2 Severity Rating Scale
-
- Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
- Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2021/10/20
- Access Count
-
10,265
No.2 Apache Log4j vulnerable to remote code execution JVNDB-2021-005429
- CVSSv2 Severity Rating Scale
-
- Level III (High)
- CVSSv2 Base Score
-
9.3
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
10.0
- Date Public
-
2021/12/14
- Access Count
-
10,196
No.3 Apache HTTP Server vulnerable to directory traversal JVNDB-2021-000090
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
5.0
- CVSSv3 Severity Rating Scale
-
High
- CVSSv3 Base Score
-
7.5
- Date Public
-
2021/10/8
- Access Count
-
7,671
No.4 Log4j vulnerable to deserialization of untrusted data JVNDB-2019-013606
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2020/1/10
- Access Count
-
6,567
No5. Multiple vulnerabilities in Cybozu Remote Service JVNDB-2021-000088
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
5.3
- Date Public
-
2021/9/30
- Access Count
-
6,411
No.6 Trend Micro ServerProtect family vulnerable to authentication bypass JVNDB-2021-002774
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/10/1
- Access Count
-
6,264
No.7 Nike App fails to restrict custom URL schemes properly JVNDB-2021-000089
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.3
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/10/8
- Access Count
-
5,971
No.8 Multiple vulnerabilities in CLUSTERPRO X and EXPRESSCLUSTER X JVNDB-2021-000097
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2021/10/29
- Access Count
-
5,763
No.9 Multiple vulnerabilities in Cybozu Office JVNDB-2021-000022
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/3/15
- Access Count
-
5,675
No.10 Information Disclosure Vulnerability in Hitachi Tuning Manager, Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center Analyzer JVNDB-2021-002810
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/10/5
- Access Count
-
5,610
No.11 Trend Micro HouseCall for Home Networks vulnerable to privilege escalation JVNDB-2021-002752
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/9/30
- Access Count
-
5,521
No.12 SNKRDUNK Market Place App for iOS vulnerable to improper server certificate verification JVNDB-2021-000085
- CVSSv2 Severity Rating Scale
-
- Level II (Medium)
- CVSSv2 Base Score
-
4.0
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.8
- Date Public
-
2021/9/28
- Access Count
-
5,395
No.13 128 Technology Session Smart Router vulnerable to authentication bypass JVNDB-2021-000091
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2021/10/18
- Access Count
-
5,297
No.14 WordPress vulnerable to cross-site scripting JVNDB-2020-006831
- CVSSv2 Severity Rating Scale
-
Level I (Low)
- CVSSv2 Base Score
-
3.5
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.8
- Date Public
-
2020/7/20
- Access Count
-
5,162
No.15 OMRON CX-Supervisor vulnerable to out-of-bounds read JVNDB-2021-003080
- CVSSv2 Base Score
-
-
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
6.5
- Date Public
-
2021/10/18
- Access Count
-
5,142
No.16 InBody App vulnerable to information disclosure JVNDB-2021-000084
- CVSSv2 Severity Rating Scale
-
- Level I (Low)
- CVSSv2 Base Score
-
2.9
- CVSSv3 Severity Rating Scale
-
- Low
- CVSSv3 Base Score
-
3.5
- Date Public
-
2021/9/28
- Access Count
-
5,141
No.17 WordPress Plugin "OG Tags" vulnerable to cross-site request forgery JVNDB-2021-000086
- CVSSv2 Severity Rating Scale
-
- Level I (Low)
- CVSSv2 Base Score
-
2.6
- CVSSv3 Severity Rating Scale
-
Medium
- CVSSv3 Base Score
-
4.3
- Date Public
-
2021/9/28
- Access Count
-
5,116
No.18 Apache log4net vulnerable to XML External Entity JVNDB-2020-005296
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
7.5
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2020/6/11
- Access Count
-
5,029
No.19 Multiple vulnerabilities in Sharp NEC Display Solutions' public displays JVNDB-2021-000081
- CVSSv2 Severity Rating Scale
-
Level III (High)
- CVSSv2 Base Score
-
10.0
- CVSSv3 Severity Rating Scale
-
Critical
- CVSSv3 Base Score
-
9.8
- Date Public
-
2021/9/17
- Access Count
-
5,023
No.20 WordPress vulnerable to authentication bypass using an alternate path or channel JVNDB-2020-006893
- CVSSv2 Severity Rating Scale
-
Level II (Medium)
- CVSSv2 Base Score
-
6.0
- CVSSv3 Severity Rating Scale
-
Low
- CVSSv3 Base Score
-
3.1
- Date Public
-
2020/7/22
- Access Count
-
4,993
Table 3-2 lists the top 5 most accessed vulnerability information among those reported by domestic product developers.
Table 3-2. Top 5 Most Accessed Vulnerabilities Reported by Domestic Product Developers [Oct. - Dec. 2021]
No.1 Information Disclosure Vulnerability in Hitachi Tuning Manager, Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center Analyzer JVNDB-2021-002810
- CVSSv2 Base Score
-
- -
- CVSSv3 Base Score
-
- -
- Date Public
-
2021/10/5
- Access Count
-
5,610
No.2 Authentication Bypass Vulnerability in Hitachi Device Manager JVNDB-2021-003660
- CVSSv2 Base Score
-
- -
- CVSSv3 Base Score
-
-
- Date Public
-
2021/11/1
- Access Count
-
4,230
No.3 File Permission Vulnerability in Hitachi Automation Director, Hitachi Infrastructure Analytics Advisor and Hitachi Ops Center JVNDB-2021-003811
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/11/5
- Access Count
-
4,223
No.4 Improper access control vulnerability in JP1/IT Desktop Management 2 - Manager and JP1/NETM/Asset Information Manager JVNDB-2021-001021
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/2/8
- Access Count
-
4,034
No.5 Information Disclosure Vulnerability in Cosminexus JVNDB-2021-001345
- CVSSv2 Base Score
-
-
- CVSSv3 Base Score
-
-
- Date Public
-
2021/4/13
- Access Count
-
4,023
Footnotes
-
(*1)
-
(*2)
-
(*3)
-
(*4)
-
(*5)
-
(*6)
-
(*7)
-
(*8)
-
(*9)
-
(*10)
-
(*11)
-
(*12)
-
(*13)
-
(*14)
-
(*15)
-
(*16)
Past Quarterly Reports
Contact information
IT Security Center,
Information-technology Promotion Agency, Japan (ISEC/IPA)