Enhancing information security

JISEC-First Time Applicant
Last Updated:Oct 4, 2010
This page offers you information to understand the outline of the workflow of IT Security Evaluation and Certification.
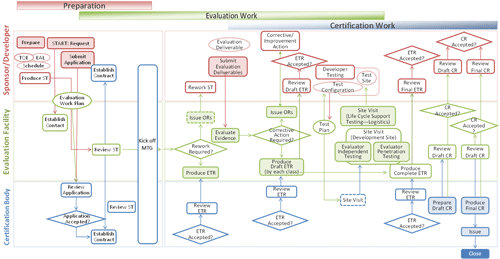
The working processes of IT Security Evaluation and Certification consist of the following four steps.
- 1 Preparation Step:
-
Necessary preparations for submitting an application for Evaluation and Certification
- 2 Evaluation Work Step:
-
Examination of the evaluation deliverables followed CEM.
- 3 Certification Work Step:
-
Review of adequacy of the evaluation.
- 4 Publication Step:
-
Publication on the JISEC Web.
Evaluation and Certification Processes
1 Preparation Step
1.1 Necessary preparations for application
To apply the certification, the applicant should be clarifying the purpose and the range of evaluation beforehand. If it is not considered enough, unnecessary expense and the man-hour are spent in the course of the evaluation and the certification.
-
To determine the suitability of the scope of TOE for evaluation and EAL.
-
To describe the Security Target.
-
To arrange the schedule.
-
To identify the deliverables needed to support the evaluation.
TOE
-
The range and EAL (Evaluation Assurance Level) of TOE (Target of Evaluation) are specified.
-
The range of TOE and EAL are related within the range of the test.
In a word, the more the range of test extends, the more cost and time for evaluation are spent.
ST
-
The evaluation period may be extended greatly by going upstream on the process in the evaluation when the maturity of ST is low at the application stage. It is necessary to complete ST at the first stage of the evaluation. The evaluation is executed based on completed ST.
Deliverables
-
Besides IT product or IT system of target for evaluation, evidential materials such as design documents used for the development, test related documents, administrator's guide, user's guide and so on are required to be evaluated.
-
Necessary materials are different according to EAL.
Schedule
-
Make a rough schedule taking the preferred time to get the certification in consideration, whether it is before its release or after the release.
-
It is necessary to consider the allocation of development resource to evaluation support work and the influence of mutually work delay in design and certification, if you plan the acquisition of certification in parallel with development.
-
Assume that items pointed out as a problem at the evaluation phase, for instance, when the vulnerability is found and it feed back to the development, may affect the development schedule.